
Ransomware: What the LockBit 3.0 data leak reveals
An administration interface instance for the ransomware franchise's affiliates was attacked on 29 April. Data from its SQL database has been extracted and disclosed
On 7 May 2024, the presumed identity of the operator of the LockBit 3.0 franchise, also known as LockBitSupp, was revealed during UK National Crime Agency and its partners' Operation Cronos: Dmitry Yuryevich Khoroshev.
One year later, to the day, the entire contents of the SQL database of a web administration interface for the company's affiliates was made public. And not just anywhere - on the ransomware franchise's websites. The irony is - they were hacked. The data was extracted on 29 April. It concerns a system that was set up on 18 December last year.
A rare light
This data provides unprecedented visibility into the activities of the LockBit 3.0 ransomware. The compilation dates of the encryption malware make it possible to adjust previous estimates of attack occurrence dates. In the case of certain known victims, they have already revealed a gap of up to 10 days between the end of the exfiltration of the victim's data and the launch of the encryption. This underlines the importance of efforts to detect such exfiltration.
This data can also be used to attribute different victims to their attackers. This grouping will be useful for analysing negotiation methods and tracking any ransom payments.
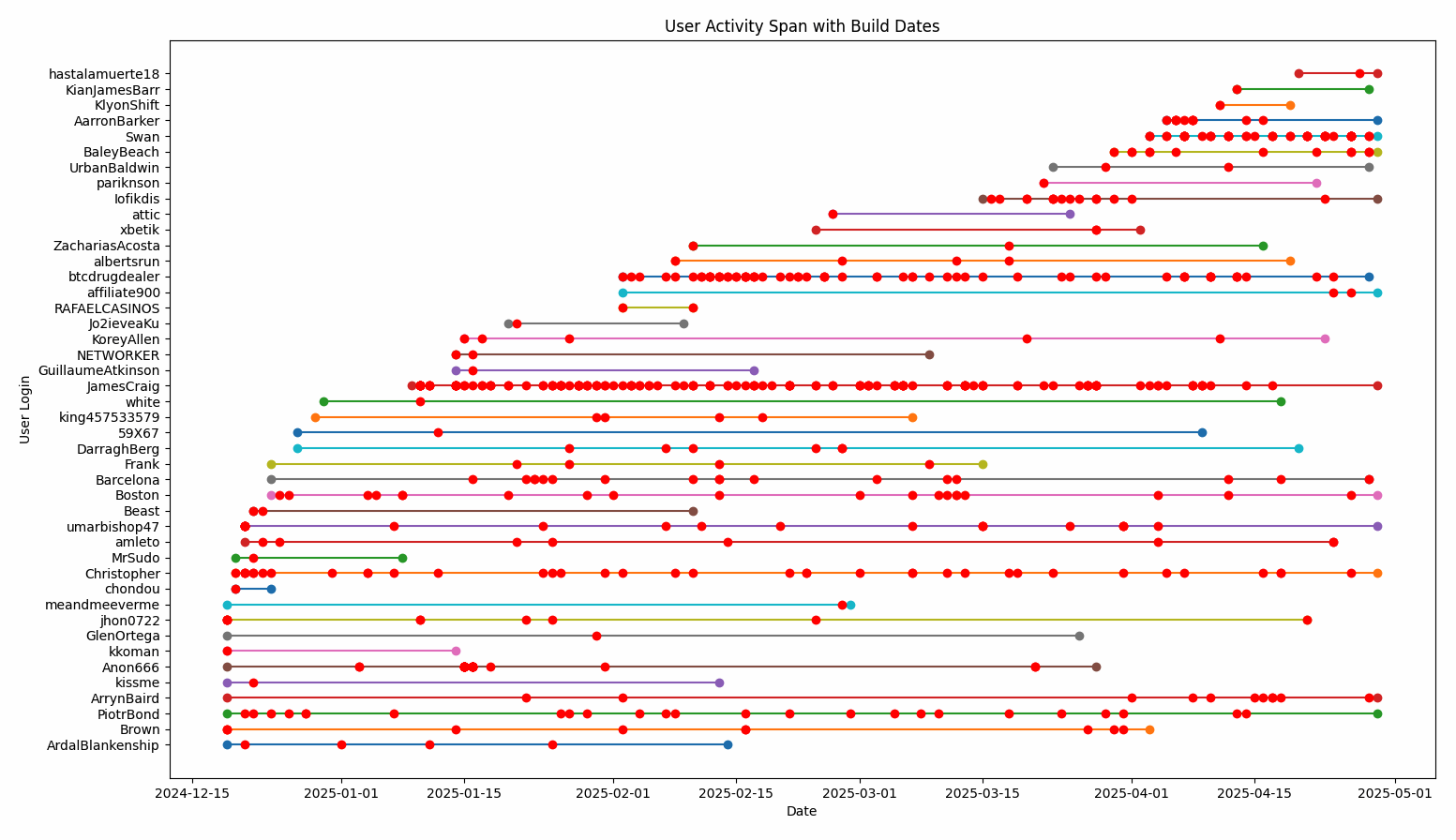 Activity of LockBit affiliates between 18 December 2024 and 29 April 2025 - LeMagIT
Activity of LockBit affiliates between 18 December 2024 and 29 April 2025 - LeMagIT
This administration interface for affiliates contained 75 user accounts, two of which were most likely used by LockBitSupp itself. No less than 35 accounts were "paused," two of which had been used against victims in Russia. The company's operator has assured that this is the reason for their suspension.
But only 44 accounts were actually used to generate ransomware and possibly launch cyber attacks. Of these, 30 were active on 29 April, but only seven appear to have been engaged in conducting attacks at that time.
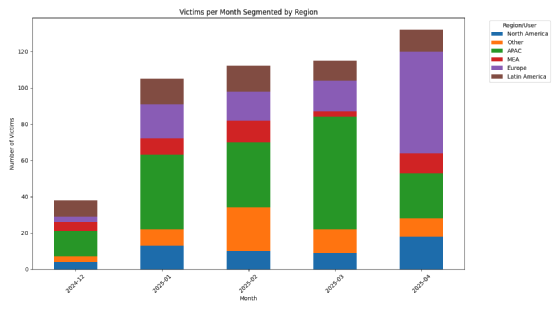
LeMagIT
A geographical spread
Research into the geographical origins of the victims mentioned reveals an unusual trend - in all likelihood, the Asia-Pacific region was the focus for 35.5% of the efforts of LockBit's affiliates over the period in question, compared with 22% for Europe, and less than 11% for North America, behind Latin America at 12%.
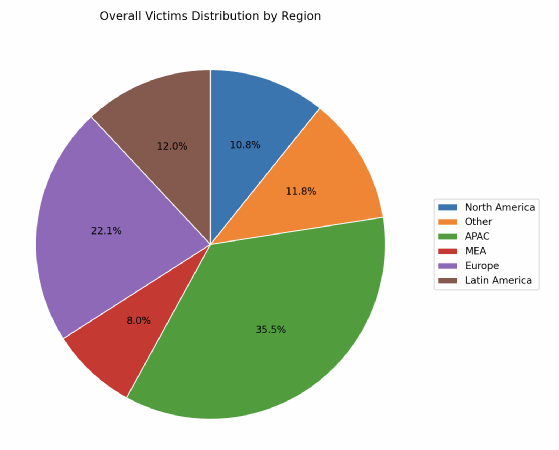
LeMagIT
But there are very marked disparities between affiliates. PiotrBond, for example, concentrated on the Asia-Pacific region, with 76% of its victims. The same applies to Umarbishop47 (81%). DarraghBerg bet equally (33.3%) on this region and Africa-Middle East. But JamesCraig also gave priority to Asia-Pacific (42%).
This geographical review also highlights the lack of observability of the threat in this region, particularly in China, which accounted for 51 victims in the sample studied. Indonesia comes a close second with 49 victims, followed by India (35).
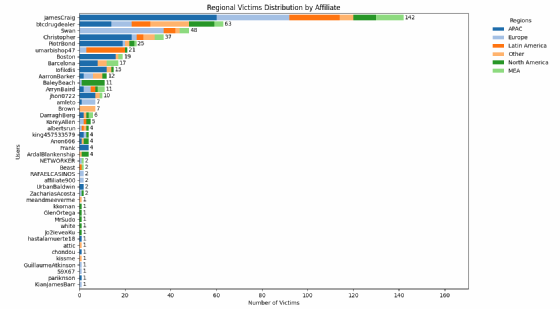
LeMagIT
The data also suggests that South Korea is globally under-represented in observable malicious activity.
This unusual geographical distribution may reflect changes in the profiles recruited by LockBit 3.0. The most active affiliates do not seem to be those who go after the most attractive victims.
The reflection of a tarnished image
The available data suggests instead that those who multiply their victims try to target potentially less mature people than others, even if they have to pay modest sums, in countries with per-capita incomes around the world average.
The negotiations observed support this analysis, with ransom amounts very frequently requested of less than $20,000.
All in all, the LockBit 3.0 banner currently appears to have only two or three active high-flying affiliates. This is only half a surprise - the Cronos international judicial operation dented the image of the mafia-like franchise. If it manages to attract anyone, its appeal is, unsurprisingly, limited.
It even makes you wonder whether some victims who refuse to pay the ransom are deliberately not being claimed on LockBit's showcase site so as not to tarnish its image even further.
And this new leak is unlikely to improve matters - it has exposed the Tox encrypted email IDs of certain affiliates, their passwords (stored in clear text), and pseudonyms with which certain open source intelligence specialists will no doubt be happy to investigate - not to mention the victims' private encryption keys.
Timeline of Lockbit activity
June 2022: LockBit ransomware gang launches bug bounty programme
August 2022: LockBit 3.0 cements dominance of ransomware ecosystem
October 2022: Ransomware crews regrouping as LockBit rise continues
October 2022: Advanced: Healthcare data was stolen in LockBit 3.0 attack
January 2023: LockBit cartel suspected of Royal Mail cyber attack
February 2023: Suspected LockBit ransomware attack causes havoc in City of London
February 2023: LockBit gang confirms Ion cyber attack as disruption continues
February 2023: LockBit cartel finally claims Royal Mail ransomware attack
February 2023: Royal Mail stands firm as LockBit leaks data and renews ransom demand
February 2023: Royal Mail refused to pay £66m LockBit ransom demand, logs reveal
March 2023: Ransomware attacks up 45% in February, LockBit responsible
June 2023: NCSC warns over ‘enduring’ LockBit threat
September 2023: LockBit ransomware gang allegedly leaks MoD data after hit on supplier
November 2023: Ransomware attack on major Chinese lender disrupts financial markets
November 2023: Royal Mail spent £10m on cyber measures after LockBit attack
November 2023: Canada’s Mounties among government employees hit by LockBit
November 2023: CISA reveals how LockBit hacked Boeing via Citrix Bleed
February 2024: Cops take down LockBit ransomware gang
February 2024: LockBit gang members arrested in Poland and Ukraine
February 2024: LockBit locked out: Cyber community reacts
February 2024: NCA trolls under fire LockBit gang leaders
February 2024: LockBit bids to save face after NCA takedown
February 2024: Inside LockBit: A ransomware gang in decline?
May 2024: NCA unmasks LockBitSupp cyber gangster who toyed with pursuers
June 2024: FBI finds 7,000 LockBit decryption keys in blow to criminal gang
August 2024: Advanced faces fine over LockBit attack that crippled NHS 111
October 2024: Unmasked: The Evil Corp cyber gangster who worked for LockBit
December 2024: LockBit ransomware gang teases February 2025 return
February 2025: A landscape forever altered? The LockBit takedown one year on
March 2025: SuperBlack ransomware may have ties to LockBit
March 2025: Advanced Software fined £3m over LockBit attack








