IT Security Purchasing Intentions 2013 - Europe
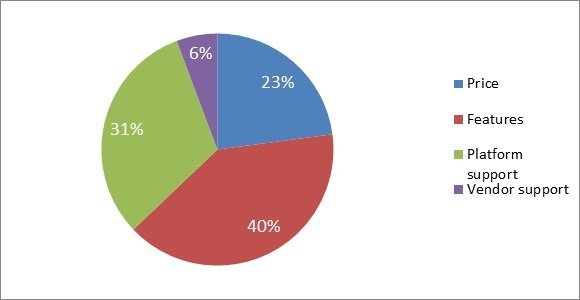
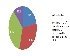
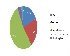
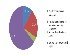
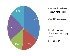
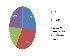
According to 40% of security professionals polled by Computer Weekly/TechTarget, the top criteria for purchasing Network access control (NAC) were features, followed by platform support (31%), price (23%) and vendor support (6%).
NAC presents similar complexity issues to data leakage or loss prevention (DLP), despite having been around for some time. About seven years after the first NAC solutions came into being, there remains a raft of barriers to its successful implementation in organisations.
"Internal politics frequently get in the way and often, NAC gets downscaled to providing protection solely at the edge of the network," said Adrian Wright, vice president of research for ISSA-UK.
"There still appears to be little consistency between vendor offerings, making head-to-head evaluation and selection difficult. This combined with interoperability woes means each NAC vendor has a preferred set of other security products they work with, and if you try and bring different products into the mix, you may find your NAC deployment can't or won't support these changes," he said.
Deploying NAC is expensive because even if the software is virtually free, it takes considerable time -- which equates to money; plus there may be hidden scalability issues, said Wright.
"You might have to upgrade or buy new switches and other infrastructure. It is possible to derive efficiency benefits from NAC quite apart from the obvious security ones.
"Justifying the cost and deployment overheads based on security needs alone is a tough call, so vendors and end users need to leverage better ROI arguments in order to justify the costs and difficulties incurred by large scale rollouts of NAC," he said.
Download our complete security survey results here.