
tiero - stock.adobe.com
Cyber criminals spread coronavirus conspiracy theories
The latest email campaigns identified by Proofpoint are spreading conspiracy theories about the coronavirus outbreak
More cyber criminal groups are turning their attention to exploiting widespread fears over the global coronavirus outbreak, with a number of further campaigns identified in the world, including some that are spreading conspiracy theories and misinformation, according to Sherrod DeGrippo, senior director of threat research and detection at Proofpoint.
This comes on top of previously reported warnings that criminal gangs are using the coronavirus to spread Emotet infections.
“In this latest round of campaigns, attackers have expanded the malware used in their coronavirus attacks to include not just Emotet and the AZORult information stealer, but also the AgentTesla keylogger and the NanoCore Rat – all of which can steal personal information, including financial information,” said DeGrippo.
“Attackers have also expanded their attacks to include credential theft. Our researchers have seen fake [Microsoft] Office 365, Adobe and DocuSign sites meant to steal credentials linked to coronavirus-themed emails.”
At first, coronavirus-themed attacks tended to target economic concerns relating to companies operating in shipping and logistics, but DeGrippo said Proofpoint is now observing more dedicated attacks on construction, education, energy, healthcare, industrial, manufacturing, retail and transport organisations. In addition to seeing previous targeting against Japan and the US, the firm is now seeing more localised attacks, particularly in Australia and Italy.
“The most notable developments we have seen are attacks that leverage conspiracy theory-based fears around purported unreleased cures for coronavirus and campaigns that abuse perceived legitimate sources of health information to manipulate users,” said DeGrippo.
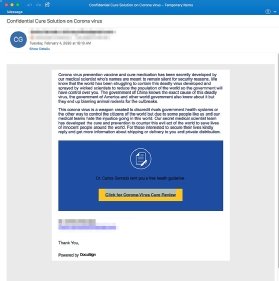
One email exploiting DocuSign (left) accuses “wicked scientists” of engineering the virus as a biological weapon and spreading it as a means of population control and to discredit rival government health services. It says that both the Chinese and US governments are aware of this, but are covering it up. It goes on to say that a vaccine and cure have been developed, which the recipient can access by clicking on a link. Needless to say, this is nonsense, and the link leads to a malicious website.
A second, and particularly well-crafted, attack purports to be an email from a president at the target business. It contains a Microsoft Word attachment with an embedded URL that takes victims to a fake Microsoft Office website where they are asked for their credentials, after which it sneakily redirects them to the genuine World Health Organization (WHO) website, making it seem more legitimate.
Another campaign takes advantage of the WHO to distribute attachments that install the AgentTesla keylogger, a strain of malware that records all inputs made on the target’s keyboard and sends the data to the attackers, which can enable them to compromise online accounts.
Yet another campaign – widely seen in Germany – attempts to appeal to concerns around factory shutdowns by masquerading as updates from suppliers, when in reality, it lures targets into installing the NanoCore remote access trojan (Rat), giving attackers full control over their system.
“These latest examples serve as a reminder that users should be watchful and exercise caution where coronavirus-themed emails and websites are concerned,” said DeGrippo. “Proofpoint will continue to monitor this situation and share updates as available.”
Read more about the coronavirus
- With coronavirus cases now reported across the world, Emotet campaigns are exploiting legitimate fears to compromise their targets.
- The coronavirus is making pandemic planning a business issue once again. The last time businesses had to consider this problem was in 2009, with the H1N1 virus.
- The coronavirus outbreak is having a direct impact on Apple’s supply chain and its Chinese retail stores and channel partners.









