Social Engineer Toolkit (SET) tutorial for penetration testers
A social engineering toolkit helps address the human element aspect of penetration testing. Learn how to use Social Engineer Toolkit with this tutorial.
The social engineering toolkit v1.0 release, code-named Devolution, is a suite of custom tools solely focusing on attacking the human element of penetration testing. Social Engineer Toolkit (SET) uses Backtrack as the framework for penetration testing. SET has been written by David Kennedy, who is also known by the nickname ReL1K. Complete details on the Social Engineer Toolkit are available at http://www.social-engineer.org
In a pen-testing scenario, alongside uncovering vulnerabilities in the hardware and software systems and exploiting them, the most effective of all is penetrating the human mind to extract the desired information. Such devious techniques are known as social engineering, and computer-based software tools to facilitate this form the basis of the Social Engineer Toolkit.
This social engineering toolkit tutorial covers backdooring of executables, and also evading antivirus software, which is implicitly handled by a few scripts within this framework. This SET tutorial also touches upon a scenario in pen testing to ascertain whether employees of the organization are aware of the security threats they face via the art of social engineering.
Introduction
To begin with, this social engineering toolkit tutorial takes an in-depth look at the spear phishing attack vectors and website attack vectors.
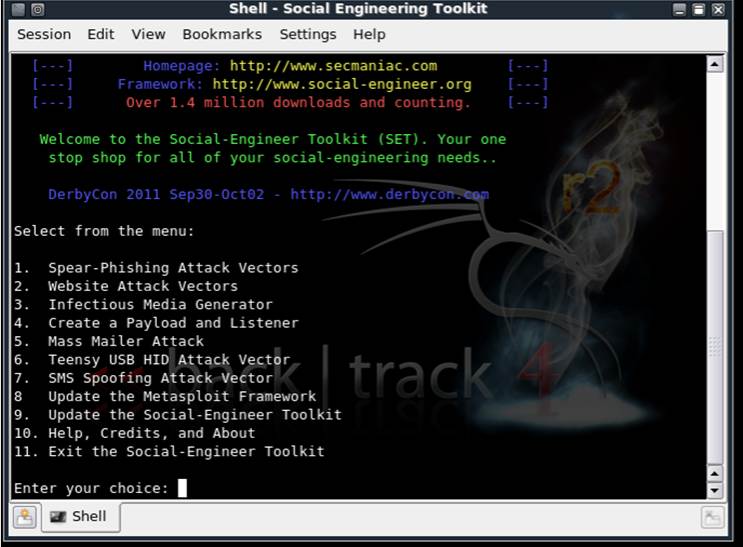
Figure 1. Opening menu of the SET framework.
A spear is a weapon with a sharp metal point at the end. And phishing is the method used by crackers to trick the user into believing that fake content and Web pages are in fact genuine.
Spear phishing is a special type of an attack wherein a specific individual is targeted, rather than a mass of users, analogous to a spear that can be used to attack only one person at any given point of time. Let us attempt such an attack using the Social Engineer Toolkit.
Selecting option 1 in the social engineering toolkit menu brings up another menu as shown in Figure 2. Choose the first option here, to perform a mass mailer attack. This attack sends an email to the victim with content that we wish to deliver.
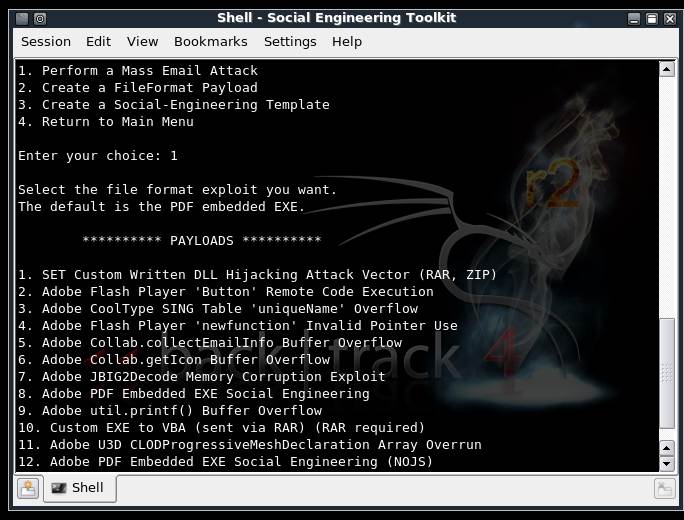
Figure 2. Attacks and available payloads.
Choosing option 10 from the list of payloads states, “Custom EXE to VBA (sent via RAR).” This means that we would send the victim a backdoored rar file.
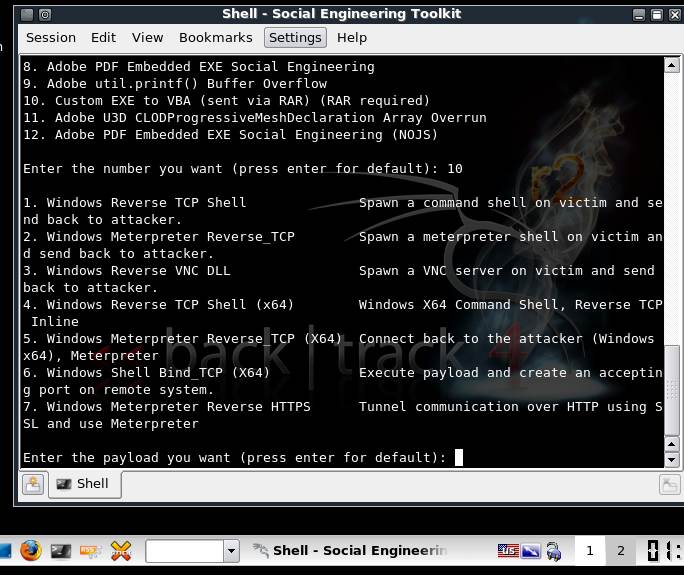
Figure 3: Shell spawning.
The various payload options available are shown in Figure 2, while in Figure 3 we can see how the Social Engineer Toolkit uses the support from Metasploit’s meterpreter extension, in spawning a shell and then controlling it in the remote system.
Once you choose the payload to send to the victim, you must provide the victim’s email id. The social engineering toolkit requires the user to login to a valid Gmail account, via which the payload will be sent. There is also a provision for using any other specified SMTP server for email.
The social engineering toolkit has predefined templates to choose from. Figure 4 shows the available templates that can be sent in the form of an email. Customized templates can also be created and saved for future use. Creating custom templates could be advantageous, as they have a higher chance of evading spam filters. Such email would reach the inbox of the victim, who would likely assume it is from a legitimate source.
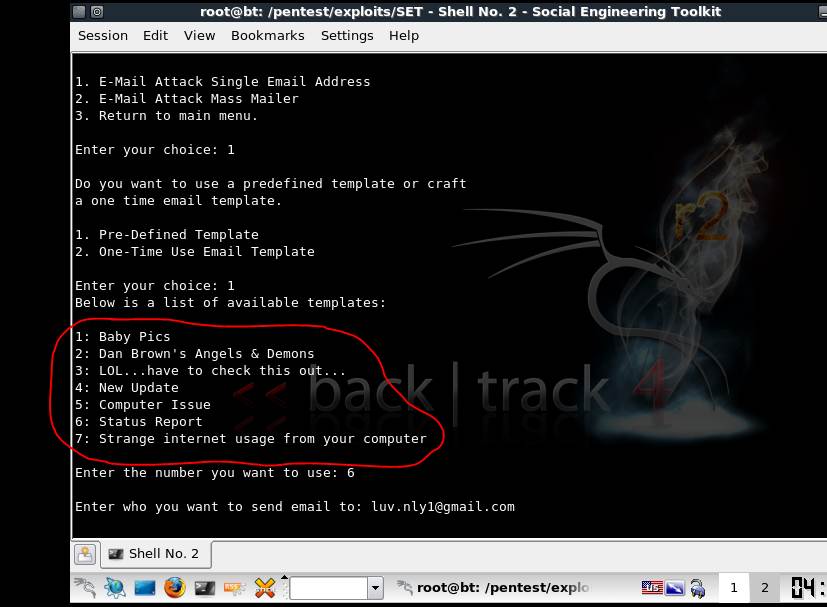
Figure 4. SET templates, which may or may not evade spam filters.
Website attack vectors
In the social engineering toolkit, the tabnabbing attack method is the one in which you can clone the entire website and harvest the keystrokes on that webpage on the fake server hosted by the Social Engineer Toolkit. When the user changes his tabs, he sees the login page and falls prey to the attack by unwittingly giving out his actual details to the attacker.
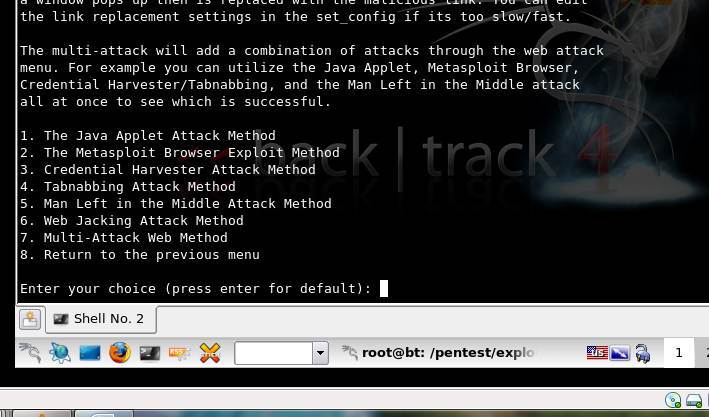
Figure 5. List of options available for website attack vectors.
Other attacks, such as the Metasploit browser exploit method, exploit the browser vulnerabilities and pwn a meterpreter shell in the victim machine thereby giving complete access to the system. The credential harvester method, as the name suggests, helps in stealing the credentials of the victim.
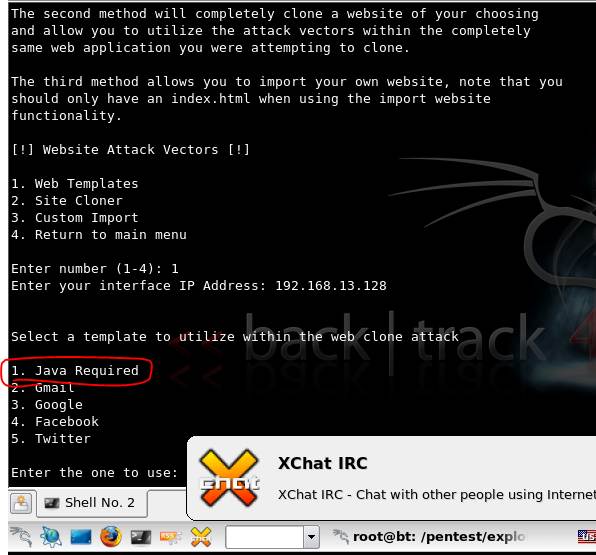
Figure 6. Java applet options available under Web templates.
Next in the social engineering toolkit tutorial, choose the template that asks the user for “Java Required”. In the subsequent menus, choose the backdoored executable shikata_ga_nai. It is rated very highly, because it evades antivirus effectively and is also quite powerful in pwning a meterpreter shell in the victim.
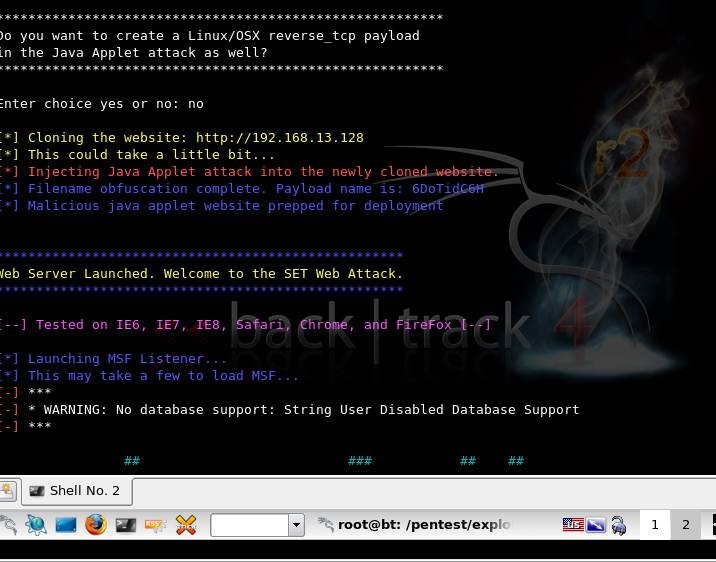
Figure 7. Web attack vector cloned at IP 192.168.13.128.
Figure 7 shows details of the cloned Web attack vector and also mentions that this attack works successfully and has been tested on IE6, IE7, Safari and Firefox. Again we see the influence of Metasploit in compromising the victim, in this social engineering toolkit.
Figure 8 shows the pop-up window in the browser, prompting the user to install a Java applet, when the URL browsed is http://192.168.13.128. Should the user click “Run”, a meterpreter shell is pwned in the system, giving the attacker control over the victim’s machine. This can be used during the penetration testing phase to test the awareness of the employees within the organization, with respect to social engineering threats.
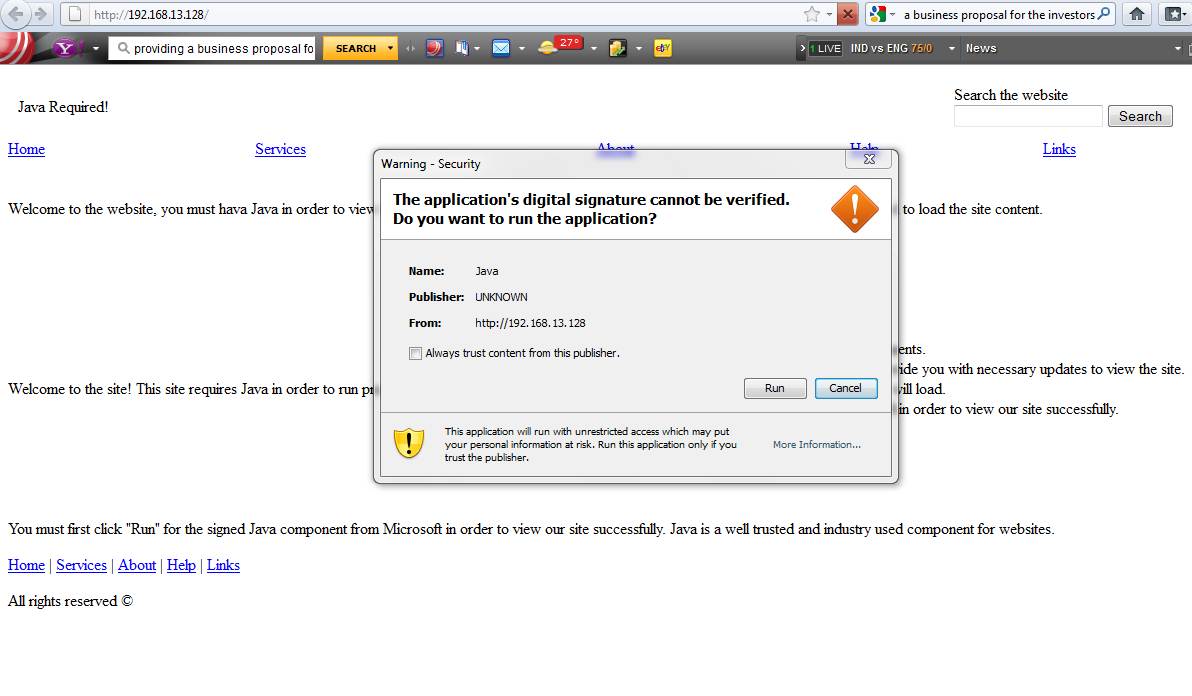
Figure 8. Deceptive pop-up to pwn meterpreter shell.
This social engineering toolkit tutorial has provided a brief introduction to the Social Engineer Toolkit. In subsequent articles, different forms of attacks will be covered. Do let us know if you would like a particular topic or attack to be covered.
 About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].
About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].
You can follow our twitter feed at @SearchSecIN









