
Jakub Jirsák - stock.adobe.com
Sharing responsibility: Why we need to work together to keep the cloud secure
The education sector has been fundamentally altered by months of lockdown, with cloud services topping must-have lists for academic staff, but now it’s time to consider security
In recent months, especially following the forced online shift through lockdown, there has been a rush across industries to adopt more cloud technology. Education is no exception, and tools such as Zoom, Teams and Microsoft 365 have shot to the top of must-have lists for educators.
Even for institutions that have already started a digital transformation journey, there will likely be conversations happening around how systems can be streamlined and security measures regulated, as more work is being completed remotely.
Security is also particularly high on the digital radar as instances of malware and ransomware attacks are becoming more prevalent, and can compromise sensitive data. A recent ransomware attack on US-based software-as-a-service (SaaS) provider Blackbaud shows how student and staff data within universities can fall prey to cyber criminals.
True cyber security relies on a secure digital infrastructure, and as some of the biggest cyber security suppliers on the planet, cloud providers are aware of the implications. Security has always been a top priority for cloud providers, and they are continually investing in making sure their infrastructure is highly secure. The use of public cloud by high-profile clients such as the military and government organisations also means the level of security across the board is of the highest standard.
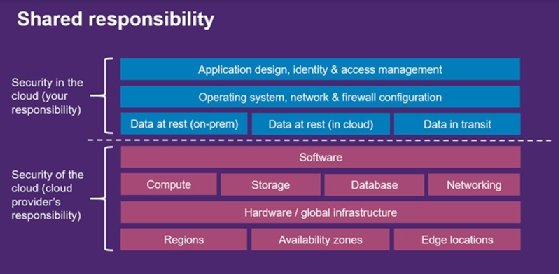
Most of the major cloud providers, such as Amazon Web Services (AWS), Microsoft and Google, use a “shared responsibility” model, which means there are various steps a user needs to take to ensure that they are using cloud services in a secure way – it doesn’t all fall on the provider.
What is a shared security model?
A shared responsibility model means that all players assume some level of security responsibility. For example, this is often a two-way split between cloud provider and customer, or a three-way split between cloud provider, customer and managed service provider. However, many players are involved in the process, and each will have a role to play in ensuring the security of data.
A good example is the evolution of AWS’s digital storage facility, S3. It used to be very easy for a user to create an S3 storage location, called a “bucket”, which is automatically open to the public, and viewable by anyone with access to the URL. If a bucket was compromised, the blame would have been directed at the user for not switching the settings to private.
For this reason, AWS has updated the service so the standard configuration is private, and the user has to manually make the bucket publicly viewable, should they choose to. AWS is, technically, not responsible for how a user configures a bucket, but has altered the infrastructure to make it easier for the user to select the most secure options.
How does a shared security model work?
There are various levels of security that come into play with a shared responsibility model. The physical security of a datacentre is the responsibility of the cloud provider, as they own the physical estate.
This means the cloud provider is responsible for regulating who is allowed to enter the centre and so on. The provider also carries responsibility for the security of the underlying infrastructure. This includes ensuring that security features are built into the cloud platform but does not stretch to elements such as password strength or enabling multifactor authentication (MFA), which are the responsibility of the user.
Users are also responsible for how they deploy cloud applications, and whether they encrypt any data stored on them. These elements use the security tools built by the cloud provider, but the configuration and use of these tools is the responsibility of the user.
For example, if a lecturer uses Microsoft Teams to gather and store coursework from students, there is an implicit trust between the student and lecturer that the lecturer will store the work in a secure way. But there is also onus on the student to upload it safely – for example, not making the document public or sending it over an insecure connection. The responsibility of Microsoft, the cloud provider of Teams, is to make sure that, in building and hosting the application, these security measures are possible and easy to implement.
With an increased move to cloud in the education sector, understanding the dividing lines within this model is essential. Moving services to the cloud doesn’t mean abdicating all responsibility – the security of cloud platforms and the data within is a collaborative effort.
To hear more about cyber security and get involved in the discussion, sign up for JISC’s security conference, running online from 3-5 November 2020. Entry is free, book your place here.











