Cyber crooks target Amazon Prime users ahead of retail bonanza
A surge in malicious domain registrations ahead of Amazon Prime Day indicates cyber criminals have set their sights on exploiting vulnerable shoppers
Almost 80% of domains containing the word Amazon are potentially dangerous, and with over 2,300 new domains linked to the retail giant registered in the past 30 days ahead of Amazon Prime Day, security researchers at Check Point Research are urging bargain-hunting shoppers to be on their guard.
The now annual Amazon Prime Day will run from 21-22 June 2021, with millions of deals and special offers pitched at Amazon’s Prime membership – which numbers about 150 million worldwide.
In the run-up to the event, Check Point’s team examined Amazon-related domains and found that one in two (46%) were malicious – clearly set up to con shoppers into giving up their Amazon credentials, email addresses and credit card details, and one in three (32%) were unprovably suspicious in some way.
Tom Kendrick, Check Point Research’s EMEA security evangelist, said there had been a 10% increase in suspect Amazon domains compared with that seen in 2020. “Prime Day is prime opportunity for cyber criminals,” he said. “The shopping event can be fun, but also dangerous for consumers.
“The danger here is being tricked into giving up your credit card info, your passwords and even your home or email address to cyber criminals. Their goal is to make money from your personal details. The tactic cyber criminals use in their deception is domain spoofing, where you click on a page that appears to be from Amazon, but you’re actually on malicious ground.”
Kendrick added: “Clearly, cyber criminals are doubling-down on Prime Day this year, as almost all the domains around “Amazon” have red flags. I strongly urge Prime Day shoppers this year to be extra cautious, to watch for misspellings, and to share only the bare minimum. I would triple-check emails that appear to be from Amazon next week, including delivery notifications. If you are unsure on the status of a delivery, go directly to the Amazon website and don’t click any links.”
Domain spoofing is a popular way for malicious actors to harvest credentials and other sensitive data or steal money. Usually, they rely on lookalike domain registrations – perhaps containing subtle spelling mistakes or substitutions – to redirect the unsuspecting to websites that contain malware or prompt them to input their information.
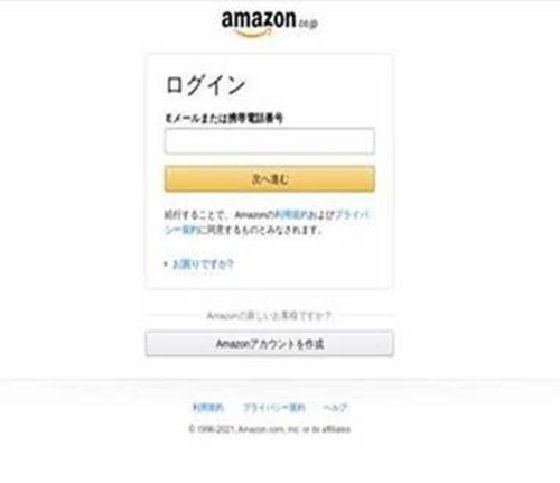
The research team shared an example of a site purporting to be Amazon Japan (see image above). In this case, it was swiftly spotted because its URL: amazon[.]update-prime[.]pop2[.]live is clearly not an Amazon website, and indeed, the website was malicious. However, with hundreds of millions of Amazon users, it is not hard to see tricks that seem easy to spot might pay off.
Besides being alert to misspellings of Amazon.com or other things that don’t look right about a URL, customers should always be sure never to shop on a site without secure sockets layer (SSL) encryption, which can be recognised by an S appended to the end of HTTP in the web address, and a locked padlock icon, typically to the left of the URL in the address bar.
Similarly, if receiving an email offer directing you to an apparent Amazon website, be mindful of standard practice to protect yourself from phishing, such as being alert to offers that seem too good to be true, or the language used – social engineering techniques are designed to take advantage of people who may be in a hurry, or more inclined to follow instructions from an apparent authority figure, maybe a celebrity endorsement or similar.
Further to this, if entering information on a website, be mindful of oversharing – few retailers should need to gather much personal data about you, but the more a malicious actor knows, the easier it is for them to hijack your identity. The safest option is to divulge the bare minimum of information.
Check Point also recommends: restricting your web shopping to your mobile data network or home Wi-Fi network, not using public Wi-Fi access to shop; using credit cards rather than debit cards, which offer more protection and less liability, and do not enable a cyber criminal to drain your bank account; and finally, creating a new strong, memorable password for your Amazon account. More guidance on creating secure passwords is available from the National Cyber Security Centre.
Read more about online fraud
- The British Retail Consortium has worked with the NCSC to develop a new cyber security toolkit pitched at retailers.
- City of London Police and National Cyber Security Centre report large uptick in threats and crime related to Covid-19 over the past year.








