Life at the edge part 2: Divide and conquer with DMZs
Learn how a DMZ works and how it can protect Web servers.

by Michael Cobb
Divide and conquer -- DMZs
A network DMZ separates and isolates a trusted network from an untrusted network by creating screened subnets. By dividing the system into segments and creating DMZs where only intermediate levels of trust exist, the system has a much greater resistance to successive compromise, thereby protecting the key resources even if other components fail. DMZs work because network traffic cannot travel between two network subnets without being routed.
@11265 Your Web servers, FTP servers, mail servers and external DNS servers should be placed in this DMZ, or "perimeter network," along with additional network defenses, such as an IDS. By putting these public services in the DMZ, you put them on a different subnet to your internal network. Your internal network is where your back-end systems such as database servers should be located. Any machine placed in the DMZ is still at risk, but if an intruder compromises the DMZ, he does not automatically have access to the internal network.
Each access point into the DMZ blocks and filters network traffic to only allow activity to or from certain network addresses, over certain ports, to pass through. Great care should be taken so that interactions with the DMZ do not expose the internal network. The barriers between each segment are controlled and screened by firewalls and routers, and protected by access control lists, strong authentication and encryption. For the ultimate in DMZ security, place each service on its own DMZ segment, configuring firewall policies to meet the needs of each server.
Network layouts
There are two DMZ network layouts we'll look at. The first, called a triple-homed perimeter network, is suitable for low-budget Web sites that do not connect to a critical internal network. The second is a back-to-back perimeter network, which is required for e-commerce and other mission-critical Web sites.
Triple-homed perimeter network
This topology uses a single firewall to separate the Internet, the perimeter network and the corporate intranet. It is also known as a single-screened subnet because the DMZ is bounded by only a single firewall with three network cards: one connected to the Internet, one to the DMZ and one to the corporate intranet (see figure 1 below). The disadvantage of this network layout is that there is a single point of failure. When ports are opened through a perimeter guarded by a single firewall, the perimeter security is unavoidably weakened. If an intruder compromises the firewall in this topology, he has access to both the server in the DMZ and the corporate intranet.
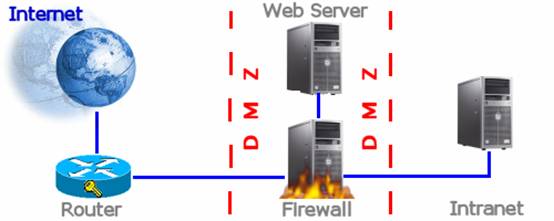
Figure 1: Triple-homed perimeter network.
Note that this topology specifies the use of a secured router between the Internet and the DMZ. Ports on this router should be locked down. Examples of ports that you would typically need open to ensure correct Web server functionality would be port 80 for HTTP and port 443 for HTTPS.
Back-to-back perimeter network
The back-to-back perimeter network topology shown in figure 2 is widely regarded as one of the most secure. The perimeter network is separated from the Internet on one side and from the internal network on the other side by using two firewalls. Each firewall has two network adapters. The external firewall has one network adapter connected to the Internet and the other connected to the perimeter network, while the internal firewall has one network adapter connected to the perimeter network and the other connected to the internal network (see figure 2 below). This provides an added layer of protection. If an intruder from the Internet compromises the perimeter network, he does not automatically gain access to resources in the internal network, as there is another barrier between the intruder and the rest of the network.

Figure 2: A dual screened subnet or back-to-back perimeter network using two firewalls.
Note that there is another secured router separating the network segments that compose the perimeter network. Although locking down this router is not as important as locking down the router connected to the Internet, ensuring that non-essential ports are closed can give additional security.
The outside firewall protects against external attacks and manages all Internet access to the DMZ. The inside firewall manages DMZ access to the internal network. This firewall should have different rules than the firewall facing the Internet, allowing only inbound application-specific service calls to reach specified systems and preventing unsolicited inbound port 80 Web traffic into the internal network. In other words, the firewall should only pass inbound traffic from a server in the DMZ that needs to communicate with one of the internal systems. For example, if a Web server communicates with a database via SQL, open TCP ports in the firewall to pass the SQL queries and responses, and block everything else. Security is further enhanced when different makes of firewalls are used on each side of the DMZ. A hacker is less likely to be able to use the same exploit to defeat both systems.
When segmenting a network for security purposes, always choose physical segmentation. A virtual LAN (VLAN) is a network segment that is logically defined and controlled by a switch that can assign its ports to two or more VLAN segments rather than have all its ports belong to the same physical segment. Although this reduces the cost of purchasing multiple switches, the segmentation is virtual. It can be removed and the security the switch provides can be easily bypassed.










