Three automated penetration testing tools for your arsenal
Automated penetration testing tools provide effective exploit libraries and processes to detect network, as well as application vulnerabilities. Our picks.
In recent times, one of the major improvements in the field of hacking has been the development of a range of tools for uncovering vulnerabilities. A vulnerability scanner can detect loopholes, but these loopholes then have to be exploited manually. On the other hand, automated penetration testing tools are equipped with quality exploits as well. Since the process of manual exploitation could produce improper results or cause the applications to crash, automated pen-test tools are considered to be more reliable and effective.
Benefits
- Automated penetration testing tools have robust, high-quality exploits that are tested and proven; the tools are also frequently augmented with additional exploits.
- They provide replicable processes that ensure consistent results.
- One can focus on the process rather than having to experiment with exploits, thus saving time. Further, the professional framework reduces the chances of testing false exploits over a particular application.
- Reports are automatically produced and are customizable.
Here is a look at three popular automated penetration testing tools — Metasploit, Core Impact and Immunity Canvas.
Metasploit
Metasploit is an open source framework created by H D Moore. It is written entirely in Ruby, and contains a comprehensive range of exploits and payloads required for testing vulnerability of a remote system. Metasploit can be used for both legitimate as well as unauthorized activities.
The basic steps for exploiting a system using the Metasploit Framework include:
1. Choosing and configuring an exploit for a specific target. Metasploit has over 300 exploits for various operating systems.
2. Checking whether the intended target system is vulnerable to the chosen exploit.
3. Choosing and configuring a payload. A payload is essentially code that will be executed once the targeted system gets compromised — for example, remote shell.
4. Executing the exploit.
There are several other options available for advanced exploiting. Metasploit also helps in testing and developing of exploits.
Figure 1. Metasploit. [Reference: http://www.metasploit.com]
Core Impact
Core Impact, another popular penetration testing tool, is available at a price. Core Impact can be used to perform exploits on a wider range of networks and Web applications than Metasploit. With Core Impact, a few clicks of the mouse are all one needs to launch the network penetration testing process, and obtain summary reports and output logs on completion.
Core Impact has a unique feature known as pivoting. This is a concept that allows a compromised host to launch exploits against other machines. This method is handy for gaining access to a target network that is blocked by a firewall. One can upload files or gain backdoor entry to the host, obtain data and then cover up one’s tracks. The basic steps for using this tool are:
- Information gathering
- Attack and penetration
- Local information gathering
- Privilege escalation
- Cleanup
- Report generation
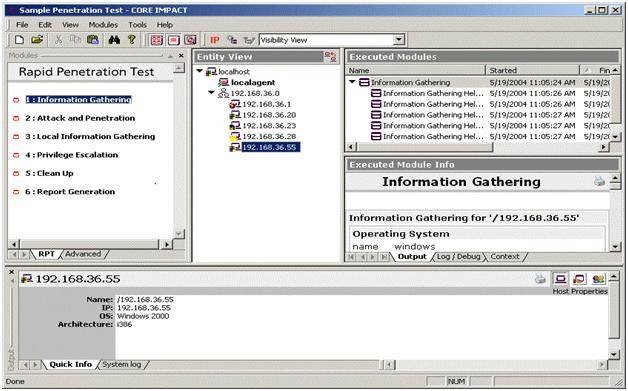
Figure 2. Core Impact. [Reference: http://www.coresecurity.com]
Immunity Canvas
Another penetration testing tool available in the market is Immunity Canvas, which is written entirely in Python. It supports both Windows and Linux platforms. One of the unique features of Canvas is its dynamic shellcode generator, known as Mosdef (“Most definitely”). This feature helps penetration testers change the shellcode dynamically, and is very useful because debugging of shellcodes inside exploits can be difficult as well as time-consuming. Canvas also incorporates a “convert slide” that can be used in the fragmentation of exploits in order to make detection by an intrusion detection system (IDS) difficult.
Canvas provides options to write new exploits or use the shellcode generator, and these exploits can be put together into a Canvas module. The exploit library is also updated regularly. Another intelligent option in Canvas is the fast, stateless scanner known as scanrand, useful for stateless host-discovery and port scanning. Extremely fast and highly reliable, it uses cryptographic techniques to prevent any manipulation of scan results.
Canvas is a great tool for penetration testing, as well as exploit development, although it is not as easy to use as Core Impact.
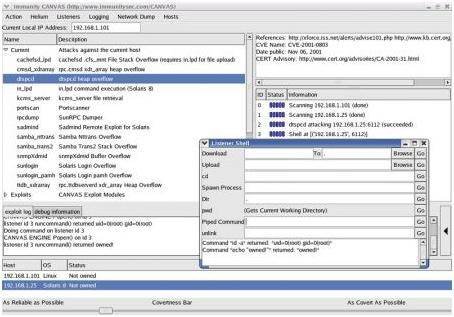
Figure 3. Immunity Canvas [Reference: http://www.immunitysec.com]
About the author: Harikrishnan R is a freelance security researcher with an interest in Web app vulnerabilities, as well as the founder of TopSecure (an infosec startup). He has also started "Internet guardians", an initiative to protect Websites.








