Leading Indian banking portals contain glaring security lapses
Even as Internet banking portals transform the way Indians bank, vulnerabilities exist in banking websites like SBI, Citibank India, HDFC Bank and ICICI Bank.
This article is based on a talk by Ajit Hatti at the Nullcon Delhi 2012 conference. Opinions expressed are the author’s own.
There is no doubt that Internet banking has proved to be a great enabler in India, with significant increases in transaction volumes each year. But just how secure are Internet banking websites in the country? There is no simple answer to this question. In fact, any answer at all will depend on the particular criteria used for evaluation.
This discussion outlines the common vulnerabilities that many Indian banking websites seem to suffer from, and highlights gaps in Internet banking security. The banks considered for this study include Citibank India, HDFC Bank, State Bank of India (SBI), Bank of Baroda (BoB) and ICICI Bank. There is definitely scope for improvement, and a need for banks to standardize on security features for Internet banking overall.
Common security problems
Here are some of the areas where security might need to be beefed up by several Indian banks to ensure more secure Internet banking:
1) Access control:
User ID generation and password generation schemes determine the level of Internet banking security to a great extent, and many banks are lacking here. For example, some banks use short/long numeric user IDs, which can be enumerated. Card numbers as user ID can also be easily enumerated. An alphanumeric, user-chosen ID is random and the most secure type of ID for Internet banking.
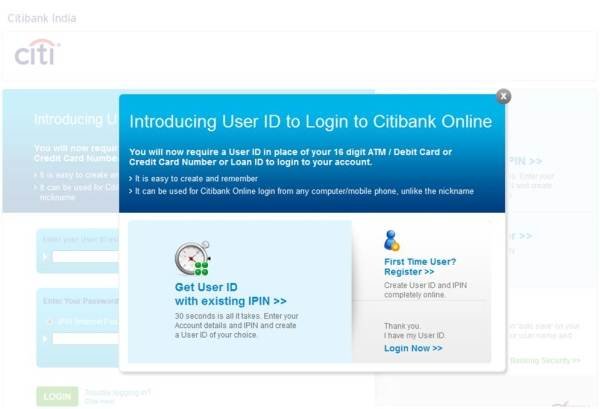
CitiBank India's Internet Banking user registration page.
Password schemes are equally important, with length and complexity criteria aiding security. Among the surveyed banks, Citibank India does not enforce password length or complexity; ICICI Bank enforces an eight-character password, but not password complexity; HDFC Bank has a minimum six-character password with no complexity. SBI used to enforce six-character passwords, but has since increased the length and complexity.
2) Security of data in motion
Banks today use SSL encryption to secure data in motion. The cipher suites used by many banks are not up-to-date. For instance, HDFC Bank runs older versions of SSL that have known vulnerabilities, making them susceptible to attacks. Of the candidate banks tested, ICICI Bank has the most robust SSL implementation, followed by SBI.
Older SSL implementations are vulnerable to several known attacks.
3) System design
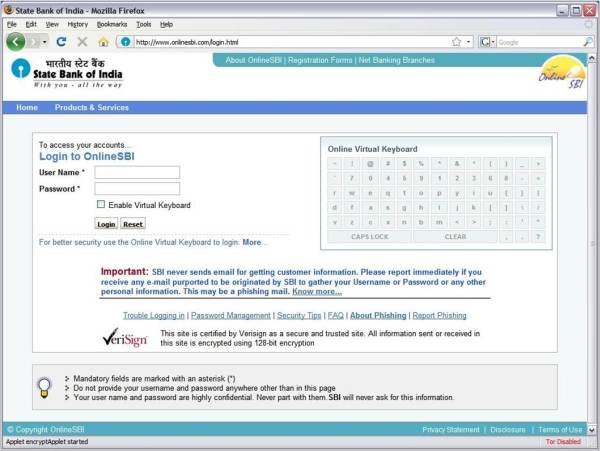
Most banks today implement anti-phishing mechanisms to protect customers and enhance Internet banking security. However, sometimes the mechanism itself is a cause for concern. For instance, HDFC Bank has a flawed anti-phishing mechanism, which can be used to reveal if an account number is valid or invalid. In SBI’s case, separate HTTP pages are not spawned during login, making it difficult for the user to determine if the page is genuine or not.
SBI's logon page had issues with spawning secure HTTPS pages.
4) Security on hostile platforms
Security on hostile platforms and the ease of regeneration of credentials is an issue with Indian Internet banking websites. On forgetting passwords, some banks only ask for date of birth and registered pin code for password reset.
Browser incompatibility or crashes also present a window of opportunity to attackers to inject malicious code. Some banks, such as Citibank India, store the password in RAM, which can be easily sniffed out on compromised machines.
Of the bank websites tested, only ICICI Bank has a mechanism for Internet banking security against hostile systems. ICICI Bank’s grid-based access control provides a predetermined grid on its debit cards, for enhanced security.
ICICI uses grid-based security using grids etched on the back of its debit cards.
5) Enforcement of best practices
Enforcement of best practices entails username schemes and password lengths as discussed, and password change policies. Other than HDFC Bank, none of the banks tested enforce a password change policy for Internet banking, even though some, such as SBI and ICICI Bank, remind users to periodically change passwords.
6) Handling hostility or DDOS attacks
Repeatedly entering incorrect passwords for banking accounts leads to accounts getting locked—something that can be used to deny service to users. Ease of enumeration of account IDs is the core flaw in this case. For example, in cases where credit card numbers are used, the first six digits are fixed and reserved for the card provider, type of card and industry.
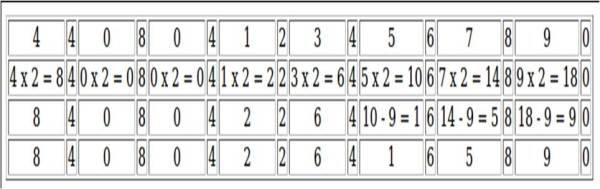
Keeping this in mind and applying LUHN’s formula can help enumerate card numbers which could be then used to launch DoS attacks against all of the bank’s accounts. Citibank India is vulnerable to such attacks, since the user IDs are card numbers. Automation is another problem for Internet banking security. None of the studied banks use “captcha” tests when accepting password changes or other sensitive details.
LUHN’s formula (MOD 10) for the card number 4408 0412 3456 7890.
7) Security as a responsibility
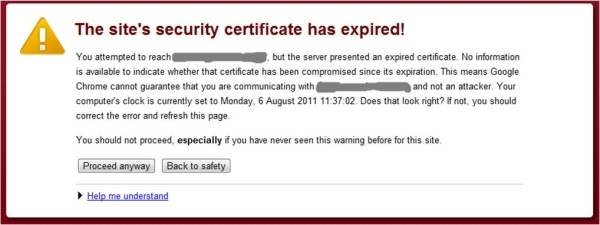
Several banks are laggards when it comes to timely renewal of digital certificates. Last year, ICICI Bank’s Internet banking portal used expired certificates for some time before ultimately renewing them. Such practices negatively condition users to accept invalid certificates.
An example of an expired certificate.
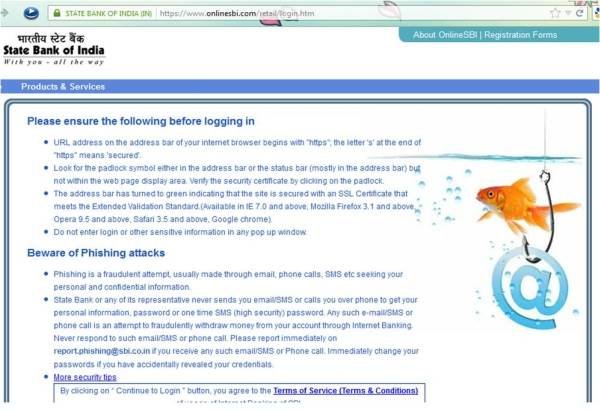
While banks have awareness campaigns, many are not designed optimally for catching user attention. For instance, SBI’s campaign tries to target users just prior to logging into the account, a point at which they are least likely to pay much attention.
SBI cautions users with an advisory page before redirecting them to the login page.
ICICI Bank fares better in this regard, with safety instructions displayed prominently on the website, check books, and so on. SBI and ICICI Bank have been observed to advise customers in an active manner on SSL safety, anti-phishing and other Internet banking security risks.
About the Author: Ajit Hatti is a security researcher and also the co-founder of null – open security community. He is currently working on the research and development of critical infrastructure security at leading Indian IT firm. Hatti is an active contributor to vulnerability research in various protocol implementations, and has been researching modern techniques for fingerprinting and application/OS detection. He loves to design puzzles and CTFs at nullcon as well as other conferences.
(As told to Varun Haran)