Windows Server 2016: A first look
The IT industry’s move towards virtualised infrastructure brought with it an obvious security vulnerability, which is that if you get access to a VM host you also get access to the VMs. You can copy or modify virtual hard drives and connect to virtual displays.
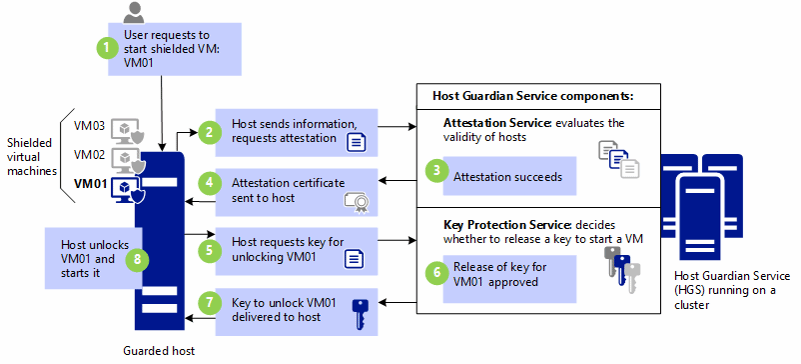
Multiple new security features in Windows Server 2016 make it possible to implement a hardened virtual infrastructure. Shielded VMs, which require a Host Guardian Service running on a separate server, can be configured to run only on specified hardware, called an “attested fabric”, identified by TPM version 2.0. The VMs must be Hyper-V Generation 2 and running Windows Server 2012 (or Windows 8) or higher. A shielded VM is encrypted, and connection to the display via the Hyper-V console is blocked, so you can only connect via the network.
Another security risk addressed in Server 2016 is the technique known as “pass the hash”, where an attacker escalates privilege by finding the hash of an administrator password and using it to access other machines. Credential Guard, which is also a feature of Windows 10, uses a virtualised container to store password hashes, isolating them from unauthorised access.
Two other key security features are time-bound administrative features, implemented using Microsoft Identity Manager Privileged Access Manager, and “just enough administration”, a feature of PowerShell which lets you configure virtual accounts for an administrative session restricted to a predefined set of roles.
Windows Server security has matured and can now be hardened to a substantially greater degree than before, but the increased complexity and infrastructure requirements mean that only a subset of Windows users will get the full benefit.