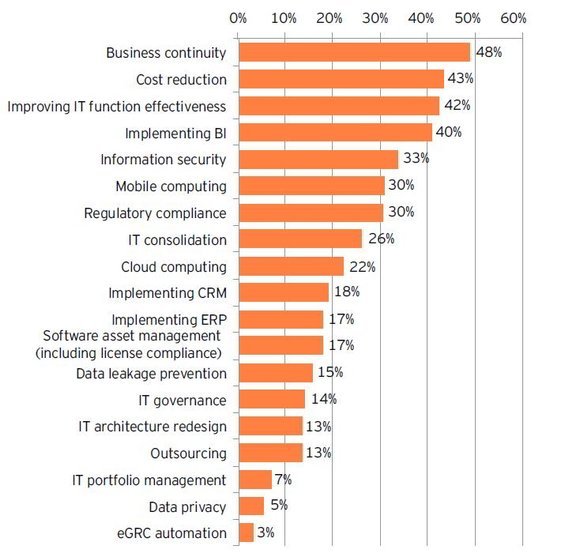
-
AI transformation is inevitable but requires change management
Enterprises are split on AI adoption speed. While some take an aggressive workforce overhaul, others preach more careful ...
-
12 top business process management tools for 2026
BPM platforms are becoming a business transformation engine as vendors infuse their tools with powerful AI and automation ...
-
News brief: Attackers gain speed in cybersecurity race
Check out the latest security news from the Informa TechTarget team
-
CISO decisions: Weighing costs, benefits of dark web monitoring
Forewarned is forearmed, and dark web monitoring can alert organizations when they're in attacker crosshairs. But for many, the ...
-
5 principles of change management in networking
Network change management includes five principles, including risk analysis and peer review. These best practices can help ...
-
How network efficiency advances ESG goals
From SDN to green electricity, network optimization plays a critical role in helping enterprises reduce emissions, cut costs and ...
-
Guide to understanding the various types of data centers
IT leaders must assess the types of data centers and align infrastructure with their business priorities, factoring in ...
-
Does your data center need a smart PDU?
A smart PDU can help you monitor and manage power flow more efficiently than a traditional PDU. Here's what you should consider ...
-
Confluent adds A2A support to fuel multi-agent AI networks
Including the open protocol enables users to build an orchestrated network of collaborative agents and could help the vendor ...
-
18 top big data tools and technologies to know about in 2026
Numerous tools are available to use in big data applications. Here are 18 popular open source big data technologies, with details...