How to implement risk-based security
Implement a simple process to identify, analyse and prioritise risk without significant investment in time or money
There has been much discussion of risk-based security, especially since security budgets and headcount have been increasingly constrained, writes Peter Wood. According to a 2013 Ponemon Institute report, adoption of this philosophy continues to grow, with 77% of UK respondents claiming a “significant” or “very significant” commitment to risk-based security. However, many organisations are still uncertain how to implement it in a practical and pragmatic way.
My response has been to create a simple process to identify, analyse and prioritise risks that can be implemented without a significant investment in time or money.
The challenge for most businesses lies in addressing three key areas of questioning:
- What are your key information assets, where are they and who owns them?
- Who has legitimate access to these assets and how are they protected?
- Who may wish to steal or damage your assets, why and how?
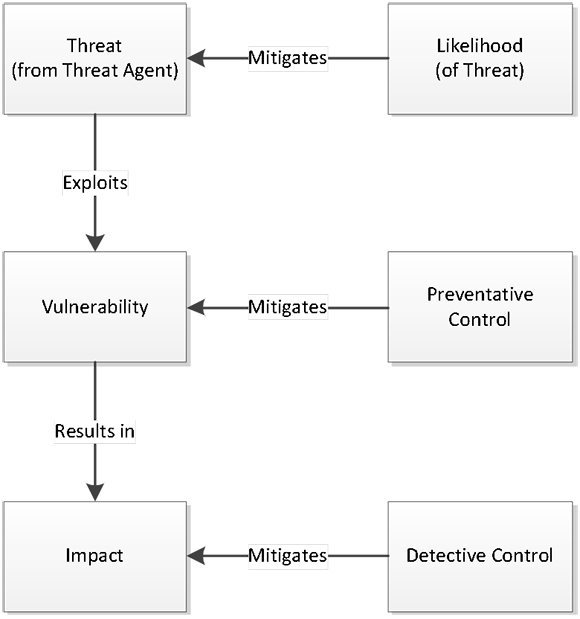
A threat analysis, in the form of a roundtable discussion led by an experienced information security practitioner, can start to answer these questions.
We start with number three, by identifying threat sources and threat agents - the adversaries who want to steal or damage your assets. These include competitors, disgruntled employees, activists, foreign governments and even non-hostile threats, such as untrained or reckless employees and business partners.
Intel developed an excellent methodology to assist with this process called Threat Agent Risk Assessment (Tara), which is available online free of charge.
The discussion around threats quickly broadens into an exchange of views on known vulnerabilities, and what information is sensitive and valuable to the business, thus addressing the other two questions. In a couple of hours, we are able to fill a flipchart with potential scenarios, and the individuals in the room begin to think in a risk-based way.
READ MORE ABOUT RISK-BASED SECURITY
- Tackle IAM with a risk-based approach, says KPMG
- Fear of cyber attack driving a shift from risk-based security, says Gartner
- Security Think Tank: Risk-based security will ease software testing challenge
- Is your information security spending in line with the risks?
- Is your information security spending in line with the risks?
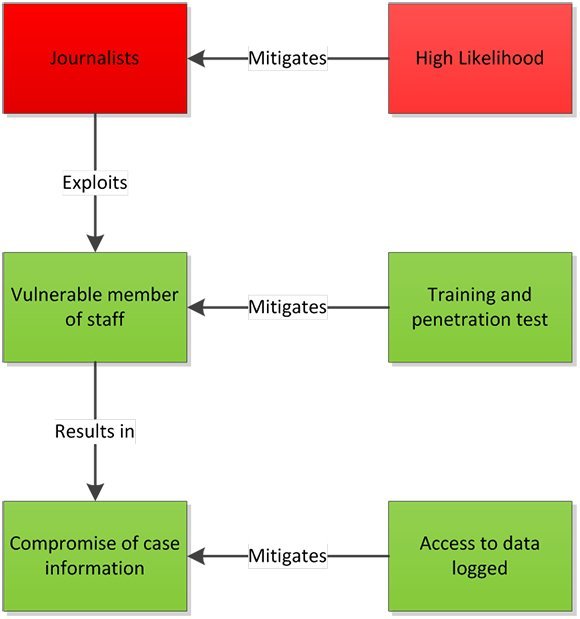
Threat scenario: Legal practice
The likelihood of a particular scenario taking place is determined in debate between security professionals and business managers, taking into account threat intelligence on the one hand and sector-specific experience on the other. The anticipated motivation of each threat agent, their respective skills and typical methods inform the discussion and allow the group to assign a risk level to each.
For example, a legal practice involved in a high-profile case may consider investigative journalists to be a threat, perhaps attempting to convince an employee to share information by coercion or deception. The motivation for this type of attack would be high and the necessary skills well-honed. As a result this would be considered a high-risk threat.
The target would be any sensitive information pertaining to the case, and the primary vulnerability would be untrained or complacent staff. In response, the business would decide to conduct a review of where the case information is located, what access controls are in place and who has permission to access the data.
An audit of the technical controls would be carried out to ensure they are working as expected, and staff would be reminded of their responsibilities to safeguard the information against any leak.
Finally, a test may be commissioned to simulate the threat, to ensure that both the technical controls and the human firewall are not vulnerable to a strongly motivated attacker.
This process is then repeated for each threat scenario, allowing resources to be applied to the risks likely to make the most significant impact on the business.
Peter Wood is CEO of First Base Technologies LLP