Web application vulnerability statistics show security losing ground
New Web application vulnerability statistics show the number of vulnerabilities is rising, despite the use of Web application development frameworks.
A survey of almost 600 custom-built Web applications revealed developers are still failing to eliminate the most commonly exploited vulnerabilities from their code, allowing attacks such as SQL injection and cross-site scripting (XSS) to occur.
You can rely on frameworks to do what they are supposed to do, but sometimes developers don’t understand what their own responsibilities are.
Michael Jordon,
Context Information Security
The new Web application vulnerability statistics (.pdf), released last week, come from London-based security services provider Context Information Security. The firm carried out penetration tests against Web applications for mainly UK organisations in both the public and private sector during 2011. It conducted a similar analysis in 2010, and said the 2011 figures show the problem of Web application security is getting worse.
The company discovered two-thirds of Web applications tested in 2011 were found to be at risk from cross-site scripting, and nearly one in five were open to SQL injection. Both techniques are commonly used by attackers to penetrate systems or to trick users into going to an infected website.
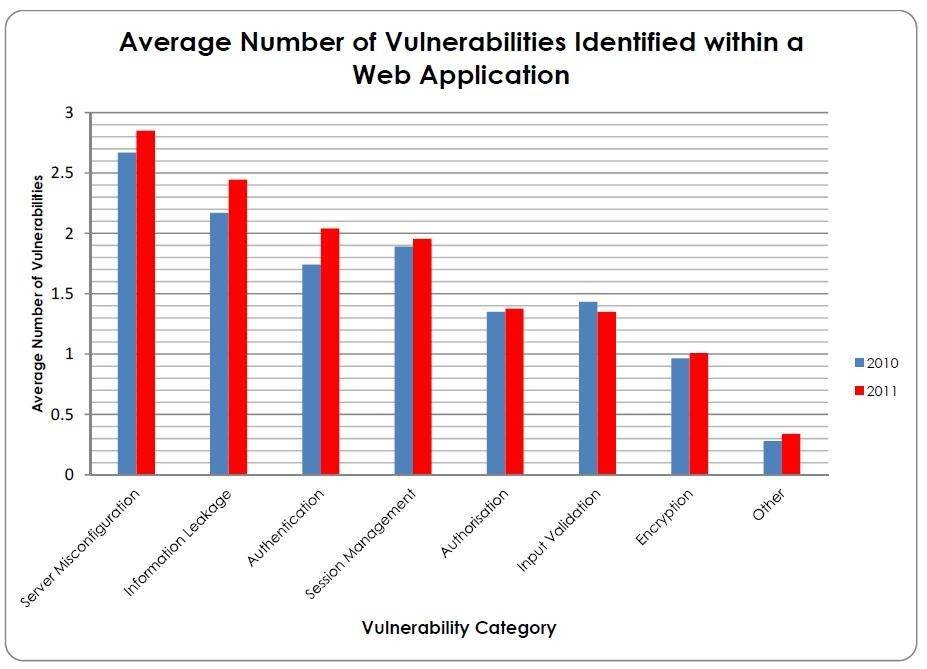
In total, Context discovered some 8,000 vulnerabilities, an average of 13.5 per application, compared with 12.5 the previous year. Server misconfiguration and information leakage topped the list of vulnerability categories that also included authentication, session management, authorisation weaknesses and encryption vulnerabilities. The only area of improvement was input validation, which the researchers attributed to increased use of development frameworks that offer built-in input validation security features.
Web applications built for the government sector contained the highest number of vulnerabilities in 2011, with more than 15 vulnerabilities per application tested. While the financial services sector had one of the lowest counts in both years, its average number of vulnerabilities per application rose slightly. The law and insurance sectors also saw a rise in the average number of vulnerabilities.
Some sectors managed to achieve improvements, with the biggest reduction in application vulnerabilities coming in media and advertising. Health care also saw a slight improvement, with the average number of vulnerabilities per application dropping from 13.5 to 11.
“I’m surprised at the level of SQL injection vulnerabilities because a lot of the frameworks over the last 10 years have evolved so you don’t have to write SQL code any more. You write at a higher level,” said Michael Jordon, research and development manager for Context.
Jordon said it was less surprising to see that cross-site scripting is still a problem because, although some of the simpler techniques have been blocked, hackers have created more sophisticated ways of executing cross-site scripting.
Although Web application development frameworks such as Apache Struts and Microsoft’s ASP.NET handle many security features automatically and do not require the developers to write special code, Jordon said this can lead to developers thinking they can forget basic security. “You can rely on frameworks to do what they are supposed to do, but sometimes developers don’t understand what their own responsibilities are. They assume the framework will do everything,” he said.
He advised companies to adopt a formal secure software development lifecycle (SDLC), so security can be incorporated into the design and development of code rather than leaving it all to a final penetration test. However, he conceded that security can sometimes get sidelined in a world of agile software development where new features can be added throughout the development cycle.
The Context Web Application Vulnerability Statistics Report for 2010-2011 (.pdf) can be downloaded from the company’s website.