Identity and access management (IAM) program implementation guidelines
The first part of this identity and access management (IAM) program guide details how to optimally structure the implementation’s foundation.
An identity and access management (IAM) program comprises a technology solution interwoven with relevant business processes, to manage the identity of users and their access to systems and applications in the organization. For any IT application, the access protocol begins with user authentication and granting appropriate access privileges based on the user’s role. The automation of these procedures is crafted by the IAM program. However, to avoid being saddled with IAM silos in different departments, the IAM program needs to be thoughtfully conceived, incorporating sound IT architectural vision. Aspects such as biometrics, federating identity, risk-based authorization and role management add to implementation challenges.
Best practices for IAM solution implementation
Enduring the IAM implementation program is not simple. Most programs tend to drift from project schedules due to implementation oversights. Here are four best practices to ensure that the IAM program succeeds and achieves its intended business objectives:
1. Embrace the overall IT vision
An identity and access management program needs to be viewed as a business solution. To unlock true business value, one needs to tie in business processes at the time of conception of the IAM program itself, with the following considerations:
• Current IT architecture and future roadmap – With existing IT and network architecture as the base, consideration should be given to current and future IT needs such as laying of service-oriented architecture (SOA), private/public cloud infrastructure, etc.
• Reflection on consolidation of business roles – Role engineering aids in simplifying IAM program implementation. It includes mapping access privileges to common business roles, identifying dead accounts, excessive privileges and redundant user groups. [See Figure 1].
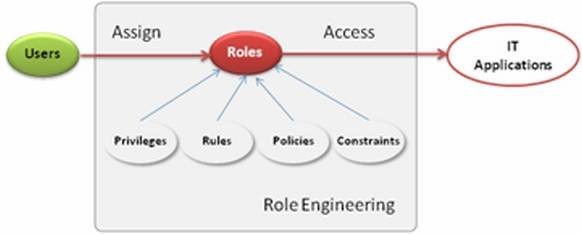
Figure 1: Role engineering prior to IAM implementation.
Example: Role engineering would help crafting 50 feasible roles and their entitlements in an organization of 500 employees. Using these 50 roles rather than the 500 user identities as subjects for authentication and authorization streamlines the business process framework and simplifies security governance.
• Auditing requirements – These should be fulfilled for compliance with standards, privacy policy and legislation, as well as provision of a governance dashboard to aid the management team’s decision-making process.
Providing enterprise-wide, integrated authentication and authorization services (such as single sign-on), support for Web services security and management, along with support for interoperability and integration between trust domains should all be part of overall IAM solution architecture. A shared IAM program across the organization is depicted in Figure 2.
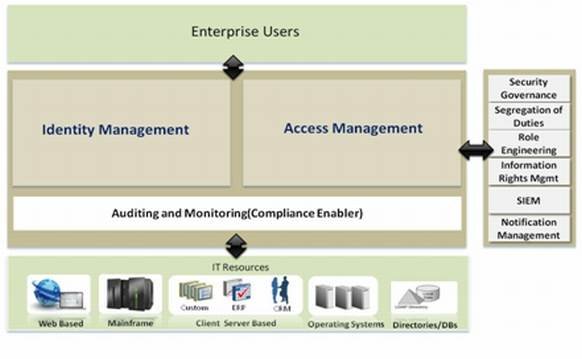
Figure 2: Enterprise identity and access management program framework.
2. Structure the foundation
Successful IAM program implementation requires a solid foundation. This includes evaluation of the completeness of the IAM product’s capability portfolio and its alignment with the organization’s IT roadmap, and risk assessment of all applications/platforms. Guidelines for performing this assessment are:
- A list of standard versus home-grown applications with version details.
- Listing operating systems, user stores, third party applications and Web servers being used. Mapping them against out-of-the-box functionality provided by the IAM solution.
- Assessment of required customization.
- Understanding of technology limitations and the capability roadmap.
It is essential to involve business and/or technical SMEs to standardize processes and define policy enforcement procedures. Immaculate deployment planning should include activities starting from defining suitable directory structure and logging mechanisms, to responsibility matrix and change management procedures.
[Don’t miss the concluding part of this article, which discusses additional best practices for successful IAM program implementation.]
About the author: Nilesh Shirke is IAM practice head in security consulting at TechMahindra. He has a masters in IS from Johns Hopkins University, and is a Sun- and Oracle IAM certified consultant. He has over 15 years experience in project delivery and security management for IT and business. His areas of expertise are security consulting and project/delivery management in the IAM domain.










