
Rawf8 - stock.adobe.com
Black Basta ransomware crew aiming for ‘big leagues’
Emergent Black Basta ransomware gang has hit more than 50 countries since bursting onto the scene earlier this year, says Cybereason
The emerging Black Basta ransomware gang has managed to hit close to 50 organisations in Anglophone countries since it started operations a few months ago, and appears to aspire to levels of infamy accorded to the likes of Conti or REvil, according to new intelligence published today by Cybereason.
Now regarded as one of the most prominent human-operated, double-extortion ransomware threats with high destructive potential, the group’s party piece is a Linux variant that targets VMware ESXi virtual machines (VMs) running on enterprise Linux servers. This aligns with its enterprise targeting and enables it to take advantage of faster encryption of multiple servers with a single command.
The Russian-speaking group also appears to have recently partnered with the QBot banking trojan/malware operation in order to spread its ransomware.
Using QBot saves time for ransomware operators as it contains capabilities that they find useful, such as the ability to conduct credential and data harvesting, to conduct lateral movement, and to download and execute payloads.
As such, this tactic has been used many times before by big players, including Conti, DoppelPaymer, Egregor and others, and it has prompted speculation that Black Basta is more than just a copycat operation, rather some kind of successor group. This is a theory that Cybereason CEO and co-founder Lior Div said may have some basis in reality.
“Since Black Basta is relatively new, not a lot is known about the group,” said Div. “Due to their rapid ascension and the precision of their attacks, Black Basta is likely operated by former members of the defunct Conti and REvil gangs, the two most profitable ransomware gangs in 2021.”
Following a series of missteps, Conti appeared to shut itself down in May, with its operatives probably moving on to different linked ransomwares, including BlackByte, Karakurt, Alphv/BlackCat, AvosLocker, HelloKitty/FiveHands and Hive. However, it it has supposedly denied any link to Black Basta.
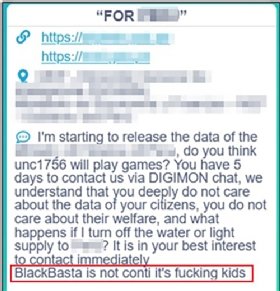
“It is pretty clear that the Black Basta gang knows what they are doing, and they want to play in the ‘big league’ of ransomware, the same league as Conti, Ryuk, REvil, BlackMatter and others,” said Cybereason senior threat researcher and threat hunter Lior Rochberger, lead author of the report.
“This may be perhaps the reason behind the speculation around being a rebrand of another ransomware,” she added. “Although it may be true, but not proven yet, it is also reasonable to believe that they were inspired by the ‘successful’ ransomware groups, specifically Conti, and try to follow their way.
“Different researchers also mentioned that there are many similarities between the two, including the appearance of the leak Tor site, the ransom note, the payment site and behaviour of the support team.”
More information on Black Basta, including indicators of compromise (IoCs), is available now from Cybereason.
Read more about ransomware
- A survey of security decision-makers in sectors regarded as critical national infrastructure reveals a disappointing attitude to ransomware threats.
- Verizon’s annual DBIR assessment of the security landscape highlights an unprecedented boom in ransomware volumes, to the surprise of nobody.
- Backups can provide a sound means of recovery from ransomware infection, but they are not 100% certain to foil attackers. We look at the limits and risks of depending on backups.










