Malware: The ever-evolving threat
The first tip in our series, "How to assess and mitigate information security threats"
Malicious software, or malware as it is commonly known, is a relatively dynamic category of threats. The techniques used to destroy data, disrupt services, and steal information have evolved to adapt to changes in security practices and countermeasures. For example, antivirus countermeasures can detect many viruses and worms by searching for patterns in the binary code that appear in the virus but not in other programs. These patterns are essentially digital fingerprints that are used to identify the threatening software. In response, virus writers developed stealth techniques to mask their malicious code (see Figure 3.1).
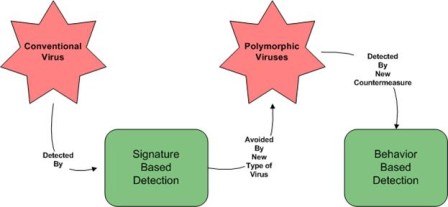
Figure 3.1: Malware and their countermeasures change in response to each other.
Today's viruses are much more complex than the early boot-sector viruses that brought malware to the attention of IT users; they are also just one of several types of malware that now pose threats to information assets. Other common forms of malware include:
- Worms—Exploit vulnerabilities in operating systems (OSs), network services, and applications to propagate and cause damage
- Keyloggers—Capture keystrokes and transmit them to the attacker
- Video frame grabbers—Copy the contents of what appears on a computer display and transmit it to the attacker
- Rootkits—Hide the presence of themselves and other malware
- Trojan horses—Appear to be legitimate but in fact contain malware such as keyloggers and spyware
The countermeasures developed for detecting viruses can often detect other forms of malware as well. Deploying antivirus programs on client devices and scanning network traffic as it enters the network are appropriate countermeasures for combating malware. In addition, locking down client devices—for example, denying most users the privileges needed to install software or update the Windows registry—can prevent the installation of malware that manages to avoid detection.
Another effective, but easily overlooked, countermeasure is security awareness training. It is common knowledge now that you should not open an email attachment sent from someone you do not know. Less well known are tips such as avoiding sites that may harbor malware, such as peer-to-peer file sharing sites, and not downloading browser plug-ins that may be Trojan horses. Keeping users aware of the changing tricks and techniques used by malware developers and cyber-attackers is an effective complement to the technical countermeasures that are essential to preserving information assets.
| For more information about malware and related in-bound threats, see Chapter 2. |

How to Assess and Mitigate Information Security threats
Introduction
Malware: The ever-evolving threat
Network-based attacks
Information theft and cryptographic attacks
Attacks targeted to specific applications
Social engineering
Threats to physical security
Balancing the cost and benefits of countermeasures
This chapter excerpt from the free eBook The Shortcut Guide to Protecting Business Internet Usage, by Dan Sullivan, is printed with permission from Realtimepublishers, Copyright 2006.










