IT pros look for ways to lock down IM
Special Report: To control growing IM threats, administrators are trying to limit which programs can be used or ban the technology altogether. But that's not always possible.
IM is forbidden in the offices of Chattanooga, Tenn.-based accounting firm Joseph Decosimo and Co., a 250-employee firm where Joyce is IT director. At the 6,000-employee Health and Human Services System agency for the State of Nebraska (HHSS), where Clifford is customer services manager in the information systems and technology services department, only one IM program is allowed and its use is restricted to within the organization.
"We have the capability to manage and filter the most popular IM programs but our policy states that IM is prohibited unless there is a strong business case for it," Joyce said. "So far, we haven't seen one, and so basically we don't allow it."
Clifford said all email, documentation and IM conversations generated from within HHSS are considered state property. Limiting IM use fits the agency policy that messaging technology be used for state business only.
These actions are rare in the enterprise today, if an exclusive SearchSecurity.com survey of 250 IT professionals from a variety of industries is any indication.
|
||||
Only 36% of those who took the survey in August said they have sound written policies to police IM usage, and more than half said at least some of their users rely on free instant messaging systems like AOL or MSN to communicate at work.
Nearly 70% said they do not use an enterprise-class IM product and they do not ban IM as Joyce's organization does. Meanwhile, only 10% of respondents said they use a third-party product to secure IM.
This, even though more than half of respondents said they consider IM a breeding ground for malware.
No will to block IM
It's not that a majority of respondents don't care who uses IM in the workplace. It's that the use of the technology exploded across their organizations before they had a chance to address the security risks. Now, IT managers can't turn back the clock because too many people have come to rely on their IM programs.
"We've had discussions about blocking IM, at least until we decide on one program for everyone," said Lane Timmons, security systems analyst for a medical research facility in Texas with 4,000 users and 7,500 Exchange mailboxes. "But it hasn't happened."
In some ways, Timmons' department is a victim of its own success. The organization hasn't suffered a major attack, and so there's no will to block IM.
"Something has to happen to make the point of why something like IM should be blocked," he said.
Locking it down
While a majority of respondents are allowing unfettered use of IM in their environments, attackers don't necessarily have an open door to their networks. That's because upper management is at least aware of the threat and approving necessary investments to secure the technology.
Nearly 60% of respondents said upper management understands the need to invest in protecting messaging systems and applications, and nearly half said their organizations plan to budget more money in the next year for that purpose.
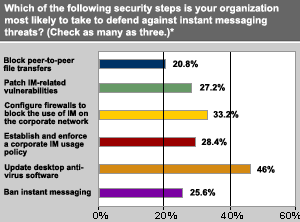
Asked which security steps they are most likely to take to defend against IM threats, 46% said updating desktop antivirus software, 33% said configuring firewalls to block the use of IM on the corporate network and more than 28% said establishing and enforcing a corporate IM use policy.
Only 26% would consider a ban on IM, and 27% would rely on any patches that might be released for IM flaws.
 |
|
One program, less worry
Several of those interviewed said they would have fewer misgivings about IM if they could limit it to one program that could be tightly controlled from within the IT shop. That's the direction Timmons is pushing toward.
"With IM, each application is different and staying atop each one can be a lot of trouble," he said. "What I'd like to do is work it into our policy that people on the network only use one IM program. It's easier to have one IM that we can control on the server side instead of letting people download whichever program they want."
Timmons' department has tested out different IM programs that could fit their needs, including the open source Jabber program. He's not sure if Jabber will be the best fit, but the department plans to keep experimenting with what's out there.
"All this is still being fleshed out and debated because we have so many groups with different interests," he said.
Defense in depth mitigates risk
Whatever their misgivings about IM, everyone agreed that the risks can be controlled with a layered security program that combines security technology with strong policies and sound computing habits among the workforce.
"Our philosophy is defense in depth," said Joyce. "We have several layers of security apparatus, hardware and software. These [tools] are scanning, filtering, trapping, blocking and quarantining in real time." He said his primary security vendors are Postini Inc. and Symantec Corp.
He is also a true believer in user education, saying the company regularly holds seminars on information security. @29815
"User education is critical, and we explain that to our users and enlist their help," he said.
Wendy Nather, information security officer for the 800-employee Texas Education Agency, relies on a combination of products form Symantec, McAfee Inc., Cisco Systems and other vendors to lock down messaging programs.
The organization also uses its own custom-made scripts to capture IM traffic in a centrally secured location.
But users' IM and email conversations aren't monitored unless there's an indication of suspicious activity, and Nather said her department's goal has been to put safeguards in place without making people feel is if they're constantly being watched.
Timmons said having policies and user education is a huge part of any security program. But no matter how good that program is there will always be risks, and management will always need time to process and understand them. His advice to other IT professionals is to be patient.
"My job is to expose those risks and show it to management, and then they decide what to do," he said. "It sometimes takes a while to get them to see the risk and turn the ship in a new direction."










