Four handy botnet detection techniques and tools: A tutorial
This tutorial will help you determine the right techniques and tools for effective botnet detection.
It’s essential to know the difference between a bot and botnet before you can identify suitable botnet detection techniques and tools. While an autonomous program automatically performing tasks in the absence of a real user is known as a bot, a network of autonomous programs capable of acting on instructions is known as botnet. A few examples of botnets include: Storm, Kraken, Conficker and Zeus, among others.
As botnets continue to gain momentum in the form of spam bots, click fraud, large-scale identity thefts and proxy nets and a large-scale distributed denial of service (DDoS) attacks, it’s proving to be a challenge to defend against these intrusive autonomous programs. Generally, a botnet may display following behavior patterns like signature-based, anomaly-based, DNS-based and mining-based. This tip discusses how to effectively use various botnet detection techniques and tools.
I. Anomaly-based botnet detection:
NetFlow analyzer:
Generally, antivirus software find it very difficult to detect worms that use dynamic codes. In this case, a DDoS attack can be detected using Cisco NetFlow analyzer.
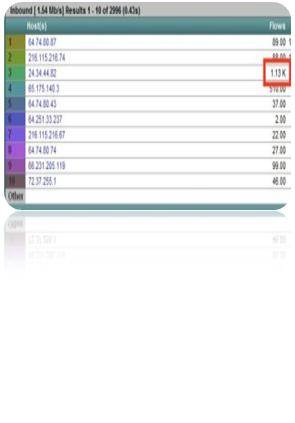
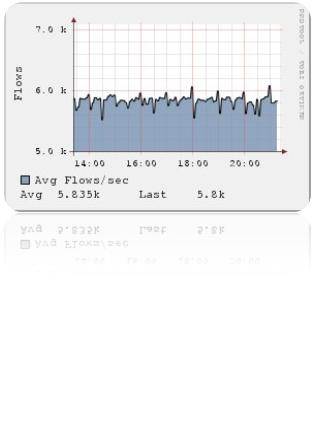
Picture courtesy: Plixer.com
First, look out for spikes in the overall flow of all your routers. Once you identify the spikes originating from the router, dig more into the origin of these anomalies, and find out the destination of these flows. This reveals whether the transfer from your routers is occurring to an unintended host.
Although anomaly-based botnet detection techniques detect unknown botnets as well, unlike signature-based detection, sometimes an IRC network may be detected. This is a botnet, but might not have yet been used for an attack.
II. Signature-based botnet detection:
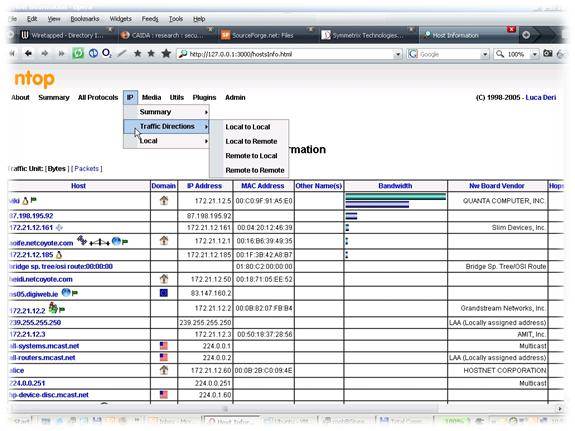
Ntop and Snort:
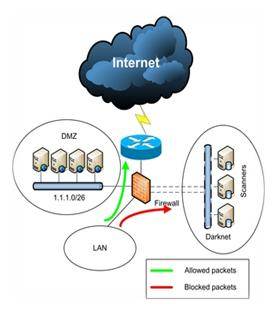
Ntop (www.ntop.org) is, ideally, a very powerful network sniffing and statistics gathering tool. When used along with Darknet, we can analyze botnets and detect them. The term Darknet refers to private or public chunk of a network that is void of any servers/services. The idea of Darknet evolved from honeypots, and is quite often underestimated. The setup looks like the figure shown below. Packets that are marked blocked are examined instead of just being discarded. Any packet in a Darknet is not a legitimate packet.
Model courtesy: Grzegorz Landecki Linuxjournal.com
Options provided in Ntop:
- Sorting packets by hosts and ports
- Network usage graphs
- Detect host OS, vendor and other details about the hosts
Snort (www.snort.org) is used along with Ntop and Darknet to log alerts. Snort is used basically for detecting botnets based on their signatures. Configuration of snort.conf is very important here. If the traffic matches any of these botnet signatures, then an alert is recorded in the log file. The particular packet can be further analyzed in Wireshark for more details. There is also a provision for writing your own signatures, making Snort very customizable for botnet detection.
Image courtesy: linuxjournal.com
III. DNS-based botnet detection
Wireshark:
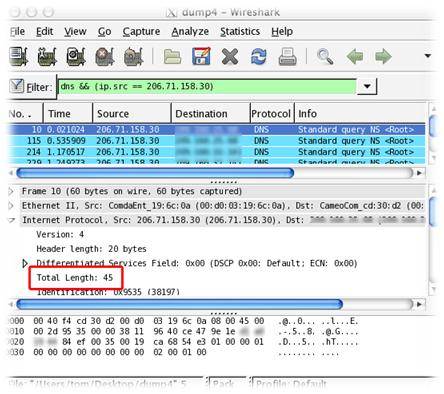
Wireshark is a very powerful tool with varied applications. We are going to use the tool for DNS traffic analysis. DNS-based botnet detection technique is based on domain name system (DNS) information generated by a botnet.
DNS capture in Wireshark – Image courtesy http://blog.tomh.us
Use Wireshark to create a CSV file using the ‘tshark -r Myfile -t fields’ command, or use a GUI tool like logparser to do this. Once done, we can retrieve the DNS name and the respective IP information from the CSV file.
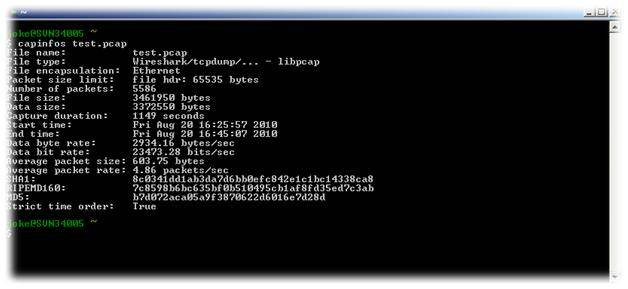
Capinfos:
Capinfos is a program that reads one or more capture files and returns all available statistics related to the input file. This package comes with the Wireshark distribution.
Usage: capinfos [options] <input file>
- capinfos prints statistics like file type, number of packets and capture duration
- uses wildcards to print information about multiple files
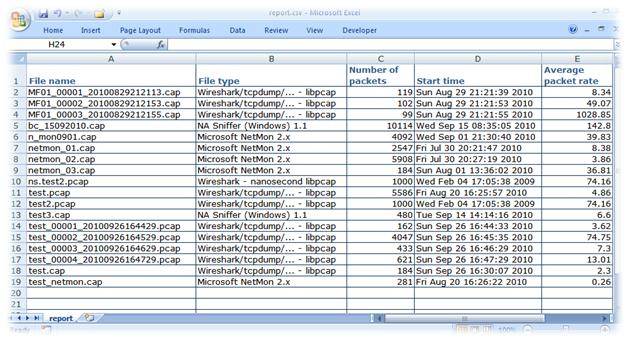
- prints statistics of all the capture files in a folder and creates a table report (CSV)
Testing capinfos
CSV file, Image courtesy: Joke Snelders
IV. Mining-based botnet detection
Botminer:
A recent development in classification and clustering models of botnet detection saw the rise of Botminer. This botnet detection tool uses a clustering algorithm, which doesn’t require any training data. It’s independent of protocol and structure, and requires no signature specification.
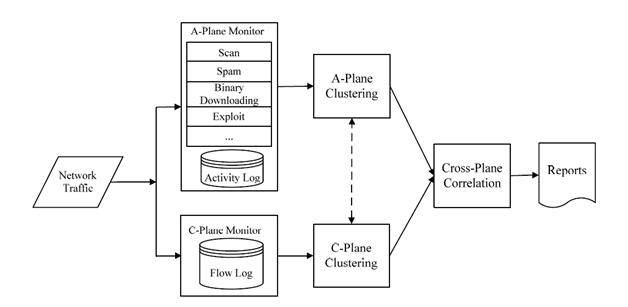
Botnets can change their command and control (C&C) content, protocols, and even C&C servers – often termed as fast flux (a technique to hide phishing and malware delivery behind the network of compromised hosts, which keeps on getting modified due to constant addition of new zombie machines). Botminer monitors two planes for botnet detection: namely C-plane (C&C communication place) and A-plane (malicious activity plane).
Clustering occurs in C-plane by finding the statistical distribution per unit time or per unit packet. Generally, a communication between a local host and a remote server consists of protocol, source IP, destination IP and destination port. In A-plane clustering, clustering occurs on the basis of activity (scan, spam, download or exploit). Ideally, the clustering algorithm is based on these distributions.
Botminer architecture: Courtesy http://www.cs.northwestern.edu
 About the author: Karthik R is a member of the NULL community. He is also the founder member of a startup named Raining Brains Security Solutions, which focuses mainly on security issues in the cyber world. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his third year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].
About the author: Karthik R is a member of the NULL community. He is also the founder member of a startup named Raining Brains Security Solutions, which focuses mainly on security issues in the cyber world. Karthik completed his training for EC-council CEH in December 2010, and is at present pursuing his third year of B.Tech in Information Technology, from National Institute of Technology, Surathkal. Karthik can be contacted on [email protected].