How to perform a cybersecurity risk assessment in 5 steps
This five-step framework for performing a cybersecurity risk assessment will help your organization prevent and reduce costly security incidents and avoid compliance issues.
Practically every organization has internet connectivity and some form of IT infrastructure, which means nearly all organizations are at risk of a cyberattack. To understand how great this risk is and to be able to manage it, organizations need to complete a cybersecurity risk assessment, a process that identifies which assets are most vulnerable to the cyber-risks the organization faces. This is a risk assessment that looks specifically at cyberthreats, so risks such as fire and flooding -- which would be included in a general risk assessment -- are not in scope.
Mitigating the risks identified during the assessment will prevent and reduce costly security incidents and data breaches, and avoid regulatory and compliance issues. The risk assessment process also obliges everyone within an organization to consider how cybersecurity risks can impact the organization's objectives, which helps to create a more risk-aware culture. So, what is at the heart of a cybersecurity risk assessment?
What does a cybersecurity risk assessment entail?
A cybersecurity risk assessment requires an organization to determine its key business objectives and identify the information technology assets that are essential to realizing those objectives. It's then a case of identifying cyberattacks that could adversely affect those assets, deciding on the likelihood of those attacks occurring and understanding the impact they might have; in sum, building a complete picture of the threat environment for particular business objectives. This enables stakeholders and security teams to make informed decisions about how and where to implement security controls to reduce the overall risk to one with which the organization is comfortable.
How to perform a cybersecurity risk assessfment: 5 steps
A cybersecurity risk assessment can be split into many parts, but the five main steps are: scoping, risk identification, risk analysis, risk evaluation and documentation.
Step 1: Determine the scope of the risk assessment
A risk assessment starts by deciding what is in scope of the assessment. It could be the entire organization, but this is usually too big an undertaking, so it is more likely to be a business unit, location or a specific aspect of the business, such as payment processing or a web application. It is vital to have the full support of all stakeholders whose activities are within the scope of the assessment, as their input will be essential to understanding which assets and processes are the most important, identifying risks, assessing impacts and defining risk tolerance levels. A third party specializing in risk assessments might be needed to help them through what is a resource-intensive exercise.
Everyone involved should be familiar with the terminology used in a risk assessment, such as likelihood and impact, so that there is a common understanding of how the risk is framed. For those who are unfamiliar with cybersecurity concepts, ISO/IEC TS 27100 provides a useful overview. Prior to undertaking a risk assessment, it is well worth reviewing standards like ISO/IEC 27001 and frameworks such as NIST SP 800-37 and ISO/IEC TS 27110, which can help guide organizations on how to assess their information security risks in a structured manner and ensure mitigating controls are appropriate and effective.
Various standards and laws such as HIPAA, Sarbanes-Oxley and PCI DSS require organizations to complete a formalized risk assessment and often provide guidelines and recommendations on how to complete them. However, avoid a compliance-oriented, checklist approach when undertaking an assessment, as simply fulfilling compliance requirements doesn't necessarily mean an organization is not exposed to any risks.
Step 2: How to identify cybersecurity risks
2.1 Identify assets
You can't protect what you don't know, so the next task is to identify and create an inventory of all physical and logical assets that are within the scope of the risk assessment. When identifying assets, it is important to not only establish those that are considered the organization's crown jewels -- assets critical to the business and probably the main target of attackers -- but also assets attackers would want to take control over, such as an Active Directory server or picture archive and communications systems, to use as a pivot point to expand an attack. Creating a network architecture diagram from the asset inventory list is a great way to visualize the interconnectivity and communication paths between assets and processes as well as entry points into the network, making the next task of identifying threats easier.
2.2 Identify threats
Threats are the tactics, techniques and methods used by threat actors that have the potential to cause harm to an organization's assets. To help identify potential threats to each asset, use a threat library such as the Mitre ATT&CK Knowledge Base and resources from the Cyber Threat Alliance, which both provide high-quality, up-to-date cyberthreat information. Security vendor reports and advisories from government agencies such as the Cybersecurity & Infrastructure Security Agency can be an excellent source of news on new threats surfacing in specific industries, verticals and geographic regions or particular technologies.
Also consider where each asset sits in the Lockheed Martin cyber kill chain, as this will help determine the types of protection they need. The cyber kill chain maps out the stages and objectives of a typical real-world attack.
2.3 Identify what could go wrong
This task involves specifying the consequences of an identified threat exploiting a vulnerability to attack an in-scope asset. For example, consider the following scenario:
- Threat: An attacker performs a SQL injection.
- Vulnerability/asset: Unpatched web server.
- Consequence: Customers' private data stolen, resulting in regulatory fines and damage to reputation.
Summarizing this information in simple scenarios like this makes it easier for all stakeholders to understand the risks they face in relation to key business objectives and for security teams to identify appropriate measures and best practices to address the risk.
Step 3: Analyze risks and determine potential impact
Now it is time to determine the likelihood of the risk scenarios documented in Step 2 actually occurring, and the impact on the organization if it did happen. In a cybersecurity risk assessment, risk likelihood -- the probability that a given threat is capable of exploiting a given vulnerability -- should be determined based on the discoverability, exploitability and reproducibility of threats and vulnerabilities rather than historical occurrences. This is because the dynamic nature of cybersecurity threats means likelihood is not so closely linked to the frequency of past occurrences in the way that flooding and earthquakes are, for example.
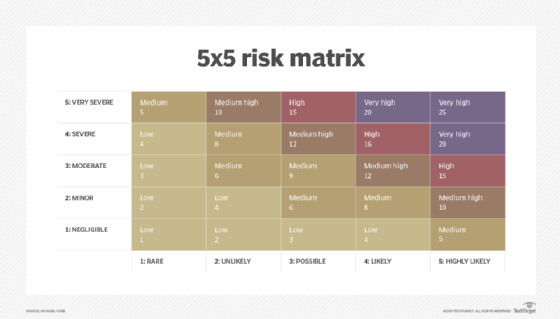
Ranking likelihood on a scale of 1 (Rare) to 5 (Highly Likely), and impact on a scale of 1 (Negligible) to 5 (Very Severe) makes it straightforward to create the risk matrix illustrated in Step 4.
Impact refers to the magnitude of harm to the organization resulting from the consequences of a threat exploiting a vulnerability. The impact on confidentiality, integrity and availability should be assessed in each scenario with the highest impact used as the final score. This aspect of the assessment is subjective in nature, which is why input from stakeholders and security experts is so important. Taking the SQL injection above, the impact rating on confidentiality would probably be ranked as "Very Severe."
Step 4: Determine and prioritize risks
Using a risk matrix like the one below where the risk level is "Likelihood times Impact," each risk scenario can be classified. If the risk of a SQL injection attack were considered "Likely" or "Highly Likely" our example risk scenario would be classified as "Very High."
Any scenario that is above the agreed-upon tolerance level should be prioritized for treatment to bring it within the organization's risk tolerance level. The following are three ways of doing this:
- Avoid. If the risk outweighs the benefits, discontinuing an activity may be the best course of action if it means no longer being exposed to it.
- Transfer. Share a portion of the risk with other parties through outsourcing certain operations to third parties, such as DDoS mitigation or purchasing cyber insurance. First-party coverage generally only covers the costs incurred due to a cyber event, such as informing customers about a data breach, while third-party coverage would cover the cost of funding a settlement after a data breach along with penalties and fines. What it will not cover are the intangible costs of loss of intellectual property or damage to brand reputation.
- Mitigate. Deploy security controls and other measures to reduce the likelihood and/or effect and therefore the risk level to within the agreed risk tolerance level. Responsibility for implementing the measures to reduce unacceptably high risks should be assigned to the appropriate team. Dates for progress and completion reports should also be set to ensure that the owner of the risk and the treatment plan are kept up to date.
However, no system or environment can be made 100% secure, so there is always some risk left over. This is called residual risk and must be formally accepted by senior stakeholders as part of the organization's cybersecurity strategy.
Step 5: Document all risks
It's important to document all identified risk scenarios in a risk register. This should be regularly reviewed and updated to ensure that management always has an up-to-date account of its cybersecurity risks. It should include the following:
- Risk scenario.
- Identification date.
- Existing security controls.
- Current risk level.
- Treatment plan, meaning the planned activities and timeline to bring the risk within an acceptable risk tolerance level along with the commercial justification for the investment.
- Progress status, as in the status of implementing the treatment plan.
- Residual risk, or the risk level after the treatment plan is implemented.
- Risk owner, meaning the individual or group responsible for ensuring that the residual risks remain within the tolerance level.
A cybersecurity risk assessment is a large and ongoing undertaking, so time and resources need to be made available if it is going to improve the future security of the organization. It will need to be repeated as new cyberthreats arise and new systems or activities are introduced; but, done well the first time around, it will provide a repeatable process and template for future assessments, while reducing the chances of a cyberattack adversely affecting business objectives.
Michael Cobb, CISSP-ISSAP, is a renowned security author with more than 20 years of experience in the IT industry.







