ComputerWeekly.com
https://www.computerweekly.com/news/2240203436/The-data-fragmentation-challenge
The data fragmentation challenge
By Tony Lock
Every IT professional is acutely conscious of the rapid rate at which business data is being created via core enterprise applications and office productivity tools, and ingested from the outside world.
The increase in data volumes to be stored over long periods of time creates significant challenges in and of itself, and these have already received considerable attention.
But the fact that this growth is usually accompanied with data now being stored on an expanding portfolio of devices is adding to the issues IT must face.
A recent survey conducted by Freeform Dynamics reveals that many organisations know, or at least suspect, that corporate data is now routinely stored in many locations.
Top of the list come the local drives of desktop PCs and laptops, where the vast majority of organisations see significant use (Figure 1).
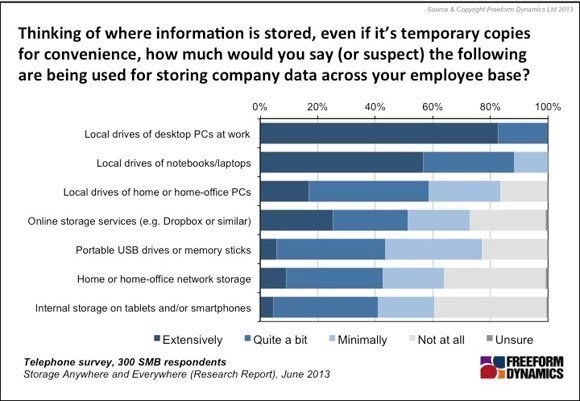
Figure 1
This is unsurprising, as the use of local hard drives to hold data, even if only for short periods of time, is almost habitual. But while this creates challenges in terms of data protection and security, it is an area with which most organisations have some experience.
However, many organisations also recognise that home PCs, USB sticks and portable hard drives, along with tablets, smartphones and online storage services such as Dropbox, are now also routinely used to hold company information.
Download resources on storage
- Computer Weekly buyer's guide to storage and backup
- Gartner: Reducing storage costs
- Storage through the looking glass
- Special report on EMC
Data everywhere, but few policies to guide where data should and should not be stored
The fact that these new platforms are used to hold corporate data is not of itself a problem. The issue is that very few organisations have policies in place covering what data can and cannot be moved to such systems nor how the data stored on them should be secured and protected.
But without any guidance on where data can be held and how it should be secured, organisations are exposing themselves to significant potential risks from data fragmentation.
The risks are easy to understand, given public concerns around data privacy, disquiet about which has been growing for some time and which recent press coverage has undoubtedly heightened.
Regulatory bodies are also focusing more attention on data storage and security, which increasingly shines a light on the fragmentation that exists. The survey indicates that these concerns are already apparent to many IT professionals (Figure 2).
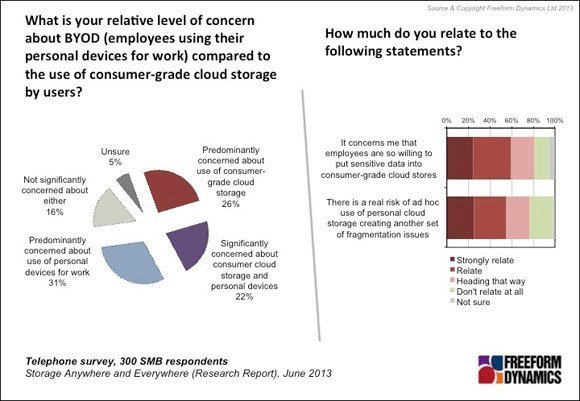 Figure 2
Figure 2
As can be seen from the above pie chart, while the dangers associated with employees using personal equipment get all the attention in the press, the concern out there about the use of consumer-grade cloud storage is at the same level as bring your own device (BYOD).
The chart on the right of Figure 2 then tells us that the concern is not just about access security. The danger is aggravating the fragmentation issue, which brings with it a broader set of problems.
Beyond security, the most conspicuous consequences of data fragmentation are usually experienced in elevated costs and operational overheads.
Most study participants report that fragmentation translates directly to wasted storage capacity due to repeated over-provisioning, with multiple copies of data driving up volumes and costs. This, in turn, leads to significant additional effort to manage the resulting complexity.
The data fragmentation challenge
With both increased risk exposure and growing storage costs to tackle, how should IT professionals be looking to manage data fragmentation more effectively?
The survey highlighted very simple steps that can be taken to both mitigate risk and better manage costs. While these actions are straightforward in an ideal world, they do need time from a range of individuals to carry them out, and that is always a challenge.
Very few organisations have policies in place covering what data can and cannot be moved to such systems nor how the data stored on them should be secured and protected
But if you are short of time or resources, you almost certainly still need to do something – either broad at a high level, or perhaps focus on key/particularly sensitive data in the first instance. Indeed, the general principle of not attempting to boil the ocean applies here as everywhere else.
Chief among the best practices identified is, the theoretically simple, "know the data you hold", along with its importance and protection requirements. Those that are doing better in managing fragmentation then carry on to actively define policies around storage management, data retention and information protection.
They key steps to take are to find all the places where corporate data is being held, conduct a high-level inventory of the information that exists, then carry out some basic classification. Once a few key categories are defined, policies concerning where key data types can be held and how they must be protected in all environments can be put in place.
It is then essential to ensure that users, at all levels in the organisation, understand what the policies mean for them. Some level of training is typically in order here, not just to make users aware of the policies, but also the logic behind them. That way, more general security consciousness is encouraged, which means users are more likely to act responsibly when a new situation not covered by existing policy is encountered.
Of course, allocating the time and effort necessary to do this is a challenge in a busy environment where resources are precious and the default motivational state with regard to security is relatively low.
Analyst reports from Freeform Dynamics
Click here to browse Freeform Dynamics analyst reports in the Computer Weekly library.
Along the way, it is therefore usually necessary to help business stakeholders understand the cost and business benefits of better data governance and management. These typically include easier access to accurate data, the basis on which more and more decisions are based, in near real time.
If this all sounds like too much trouble, then we would encourage you to stop, think and discuss the matter with those running the business. We are only seeing the beginnings of the data fragmentation challenge at the moment, and unless the issues are recognised, the danger is that you will totally lose control in a relatively short space of time.
Tony Lock (pictured) is programme director at Freeform Dynamics.
13 Aug 2013